Definitions
Access clear, concise explanations of key terms, concepts, and jargon across cybersecurity, compliance, and technology. Quickly understand complex ideas with straightforward definitions and examples to build your knowledge confidently.
Ransomware Attacks Explained: How They Work & How to Stop Them
Ransomware attacks continue to rise globally, targeting businesses of all sizes. This guide explains how ransomware works, the latest tactics used by attackers,...
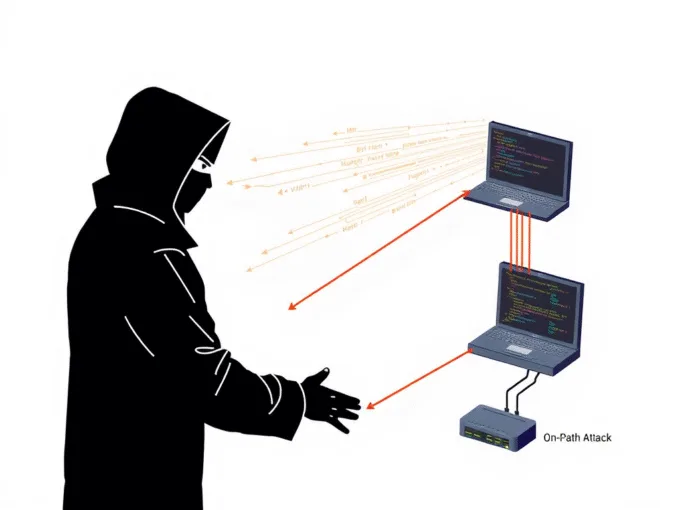
ByKumar SNovember 29, 2025What is an On Path Attack? Risks and Proven Ways to Stay Safe
What is an on path attack? Learn how cybercriminals intercept your data mid-transit, why it's dangerous, and proven steps to keep your devices...
ByKumar SMay 2, 2025Man in the Middle Attack (MITM): 7 Alarming Facts About This Proven Cyberattack Technique
Man-in-the-Middle (MITM) attacks secretly intercept communication between users and systems—stealing data without either party realizing it. This guide exposes 7 alarming facts about...
ByKumar SMay 2, 2025Social Engineering: Understanding, Preventing, and Mitigating
Social engineering remains one of the most dangerous cybersecurity threats because it targets people—not systems. This guide breaks down how social engineering works,...
ByCyberTech JournalsApril 9, 2025Understanding and Mitigating Insider Threats in 2025: A Comprehensive Guide
Discover how to identify, prevent, and respond to insider threats in 2025. Learn actionable strategies and best practices to protect your organization from...
ByKumar SApril 8, 2025What is Zero Trust Architecture? A Comprehensive Guide for 2025
In an era where cyber threats are becoming increasingly sophisticated, traditional security models that rely on perimeter-based defenses are no longer sufficient. What...
ByKumar SFebruary 17, 2025Malware Mayhem? 7 Proven Ways to Protect Yourself Effectively!
Have you ever felt that tiny shiver down your spine when you hear about another cyberattack or a new type of virus spreading...
ByKumar SJanuary 11, 2025What Is Ransomware and How Does It Work?
In today’s digital landscape, ransomware has emerged as one of the most pervasive and destructive forms of cybercrime. This malicious software encrypts a...
ByKumar SJanuary 6, 2025