Awareness
Protect Account from Password Leaks and Data Breaches
Let’s delve into the critical steps to protect your accounts from password leaks and safeguard your organization’s digital assets. In today’s digital world,...
ByKumar SJuly 4, 2025Data Loss Prevention (DLP) in 2025: How to Safeguard Your Sensitive Data
In today’s hyper-connected world, data isn’t just another business asset—it’s the bloodstream of the digital economy. And like blood, when it leaks, the...
ByKumar SJuly 3, 2025The Hidden Costs of Ransomware Attack on Your Business
In the heat of a ransomware attack, businesses often face a single agonising question: should we pay the ransom? But the ransom demand...
ByKumar SJuly 2, 2025A Practical Guide to Phishing Awareness for Employees
In today’s digital-first business landscape, phishing is more than just a nuisance—it’s a serious threat to your finances, your reputation, and your data....
ByKumar SJune 30, 2025Importance of Network Segmentation in Modern Cybersecurity
In today’s threat landscape, assuming your internal network is secure just because it sits behind a firewall is a dangerous fallacy. Cybercriminals are...
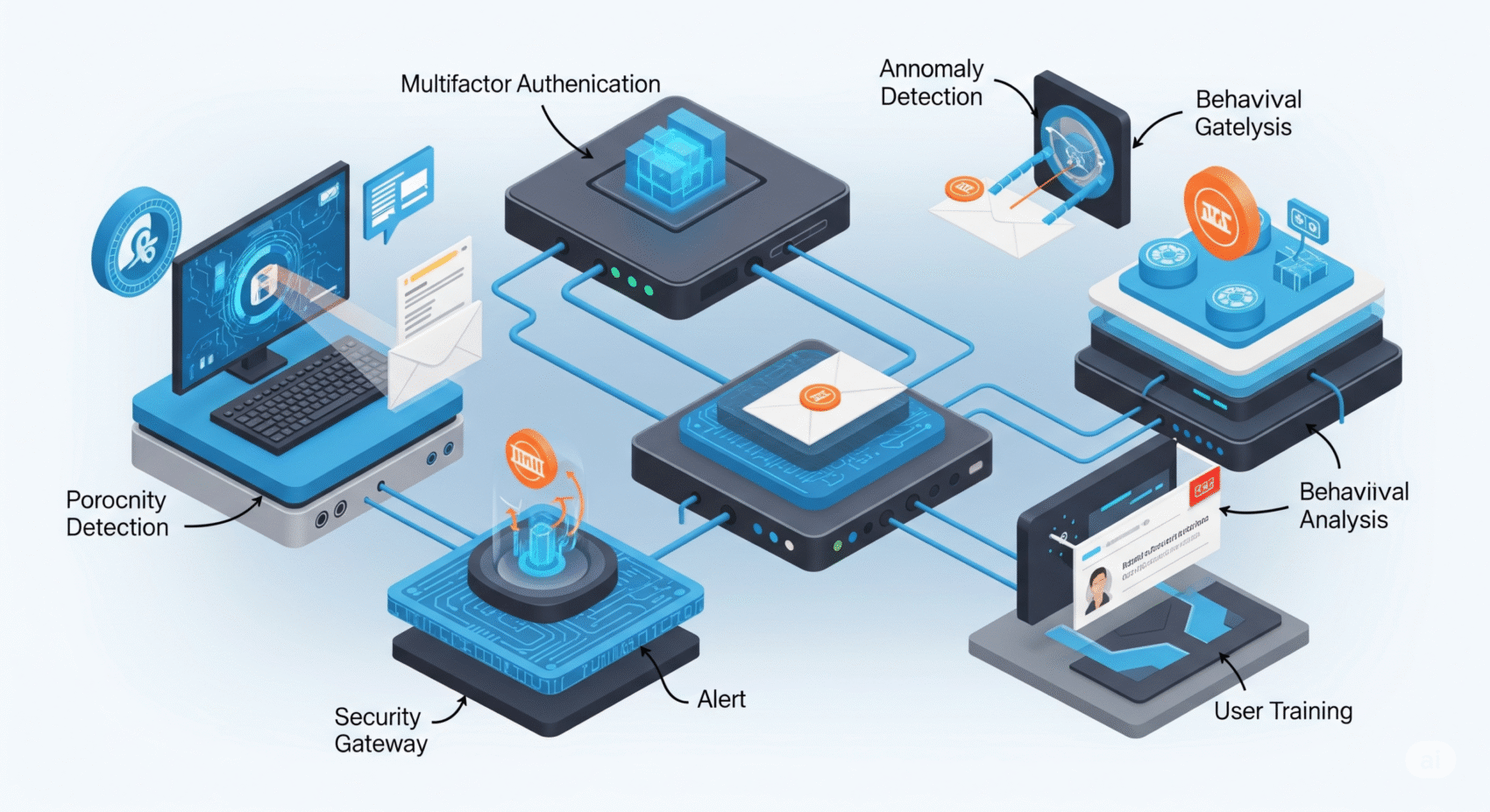
ByKumar SJune 3, 2025Strengthen Phishing Defence Mechanisms: Practical, Layered Protection for Enterprise
In today’s fast-paced digital world, businesses face a constant barrage of cyber threats. Among these, phishing attacks stand out as one of the...
ByKumar SJune 3, 2025Cyberwarfare in the Age of AI: New Weapons, New Rules
Artificial Intelligence (AI) is no longer a passive tool in the world of cyber conflict. It’s a weapon, a shield, and in some...
ByKumar SMay 20, 2025What is Pig Butchering Scam? The Disturbing Truths You Must Know
What is pig butchering scam? Discover disturbing truths about this manipulative online fraud targeting crypto investors and dating app users.
ByKumar SApril 30, 2025