Introduction
In today’s hyper-connected world, data flows continuously between devices, apps, and servers. But what if that flow isn’t as secure as you think?
Enter the on path attack—a sophisticated cyber threat where an attacker quietly inserts themselves between two parties communicating online. You may be checking your bank balance, sending a work email, or logging into your health portal—unaware that someone is watching, and possibly modifying, every byte of data.
So, what is an on path attack, and why should it be on your radar? Let’s break it down.
What is an On Path Attack?
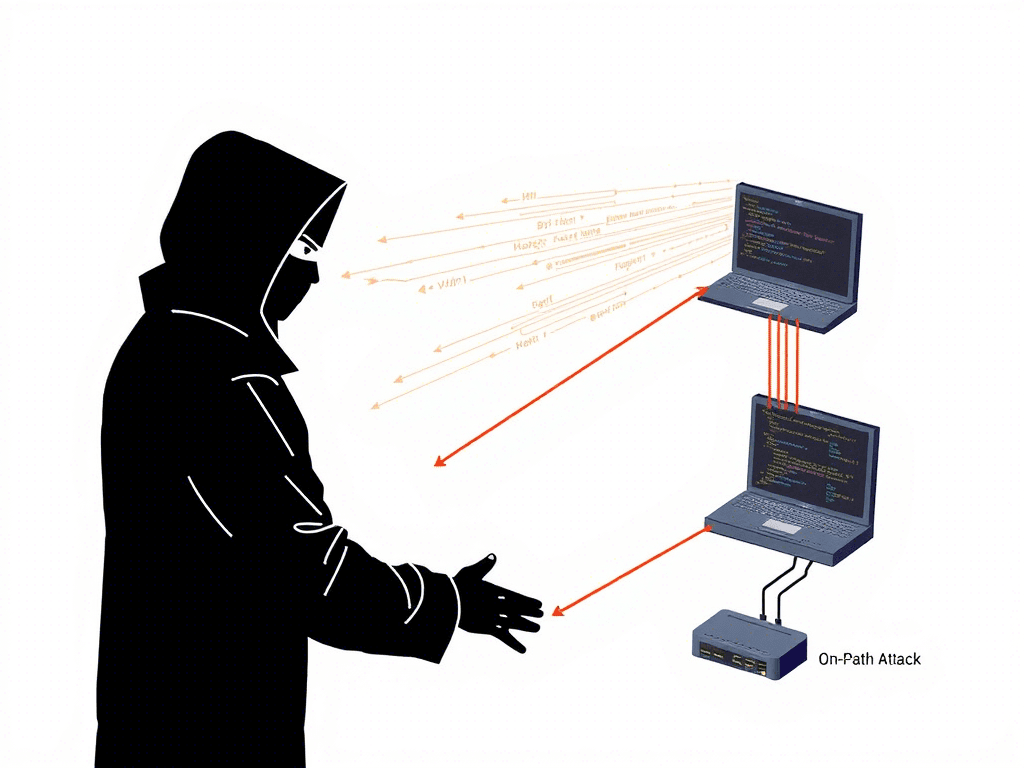
An on path attack—previously known as a Man-in-the-Middle (MITM) attack—is a form of cyberattack in which a malicious actor intercepts, relays, or alters communications between two parties who believe they are directly connected.
Unlike brute-force or ransomware attacks that draw immediate attention, on-path attacks are stealthy, persistent, and extremely dangerous. Attackers often gain access through compromised networks, especially public Wi-Fi, or by exploiting weaknesses in DNS, SSL/TLS, or session tokens.
According to CISA, on-path attacks can target any kind of data transaction, including logins, financial transactions, and private communications.
On-Path Attack vs. Man-in-the-Middle (MITM)
Although the terms are often used interchangeably, “on-path attack” is considered the modern, inclusive term for the same class of exploits previously known as MITM attacks.
The terminology shift is supported by cybersecurity institutions such as OWASP, which still lists MITM as a critical attack vector, often overlapping with broader man-on-the-side and replay attacks.
How On-Path Attacks Work
To understand what is an on path attack, it’s essential to grasp its mechanics.
Step 1: Interception
Attackers use techniques like ARP spoofing, DNS poisoning, or rogue Wi-Fi hotspots to place themselves in the communication path between two systems.
Step 2: Eavesdropping or Tampering
Once inserted, they can:
- Passively monitor traffic (e.g., read emails or capture login details)
- Actively alter data in transit (e.g., redirect users to fake login pages)
Step 3: Exfiltration or Exploitation
Captured data can be sold, used in credential stuffing, or serve as the first stage in a more significant compromise.
Real-time attacks are made more dangerous through automation tools like Ettercap and Wireshark, which enable attackers to analyse and manipulate traffic efficiently.
Common Techniques Used in On-Path Attacks
Several tactics make these attacks highly effective:
1. ARP Spoofing
Attackers send fake ARP (Address Resolution Protocol) messages to associate their MAC address with a legitimate IP, diverting network traffic.
2. DNS Spoofing
By corrupting DNS resolution, attackers reroute traffic to fraudulent websites. Cloudflare explains how this undermines trust in website identities.
3. SSL Stripping
Tools like SSLStrip downgrade HTTPS connections to HTTP, exposing sensitive credentials in plaintext. This is particularly effective on unsecured public networks.
4. Wi-Fi Honeypots
Attackers set up rogue access points with names like “Free_Airport_WiFi” to lure users and intercept all traffic.
5. Session Hijacking
Session cookies can be stolen and reused to impersonate a legitimate user without needing their password.
Shocking Risks of On-Path Attacks
- Invisible to Users
Unlike phishing, victims receive no visual clues that data is compromised. - Bypasses Basic Encryption
Weak SSL validation and lack of certificate pinning can render HTTPS protection ineffective. - Public Wi-Fi Becomes a Trap
Airports, cafes, and co-working spaces are often playgrounds for cybercriminals. - IoT Devices Are Sitting Ducks
Smart devices often lack updated firmware and encrypted communications, as highlighted by ENISA. - Corporate Espionage
Sophisticated actors use on-path attacks to gather intellectual property from rival firms or governments. - Data Integrity Is at Risk
Beyond stealing data, attackers can alter information in real time—like modifying invoice numbers or redirecting payments. - Used in APT Campaigns
Advanced Persistent Threat (APT) groups like APT28 and Turla have deployed on-path strategies as part of long-term espionage campaigns.
High-Profile Real-World Examples
🛠️ Superfish Malware (Lenovo, 2015)
Lenovo shipped laptops with adware that used a self-signed certificate to intercept HTTPS traffic. This enabled a form of on-path attack that affected encrypted browser sessions.
🛰️ Turla Group Satellite MITM Attacks
The Russian-backed Turla APT used satellite-based internet links to launch on-path attacks, obscuring their location and making attribution difficult.
🍍 Wi-Fi Pineapple
Ethical hackers and attackers alike use the Wi-Fi Pineapple to create rogue hotspots for capturing network traffic.
How to Detect an On Path Attack
Though stealthy, on-path attacks leave behind digital breadcrumbs. Here’s how to detect them:
- Frequent SSL certificate warnings or unusual prompts
- Unexpected redirects to non-secure websites
- ARP table inconsistencies, such as duplicate IPs or MAC addresses
- Intrusion Detection Systems (IDS) like Snort can identify anomalies in network packets
- Behavioural anomalies flagged by modern EDR/XDR platforms (e.g., CrowdStrike, SentinelOne)
Proven Strategies to Prevent On-Path Attacks
1. Use a Reputable VPN
A Virtual Private Network encrypts traffic end-to-end, making it unreadable to on-path attackers. Tools like NordVPN or ProtonVPN are recommended.
2. Implement SSL/TLS Everywhere
Ensure your website enforces HTTPS with a valid, trusted certificate. Use SSL Labs to test configurations.
3. Apply DNSSEC
DNS Security Extensions protect DNS queries and responses from spoofing attacks. Supported by ICANN, this is critical for domain owners.
4. Educate End Users
Training employees and individuals to spot rogue hotspots and avoid suspicious certificates is key. phishing-techniques covers this extensively.
5. Use MFA
Multi-Factor Authentication ensures that even if credentials are stolen mid-transit, the attacker still can’t log in without the second factor.
6. Enable Certificate Pinning in Apps
This prevents mobile or desktop apps from accepting fraudulent certificates.
7. Keep Firmware & OS Updated
Many routers, IoT devices, and software platforms release security patches that close vulnerabilities exploited in on-path attacks.
Final Thoughts
Now that you understand what is an on path attack, it’s clear why cybersecurity professionals treat this threat with urgency. From stealing data to quietly altering digital conversations, the power of on-path attacks lies in their invisibility and versatility.
The good news? With awareness, updated tools, and smart cyber hygiene, you can avoid becoming the next victim. Whether you’re managing a corporate network or simply browsing in a café, always assume someone might be listening—and act accordingly.
FAQ: What is an On Path Attack?
What is an on path attack in plain terms?
It’s a cyberattack where someone secretly monitors or alters communication between two systems or users who think they’re speaking directly.
Is an on-path attack the same as MITM?
Yes, “on-path attack” is a modern term for MITM. It’s used to remove gendered language and better describe the technical nature.
How do attackers perform on-path attacks?
They use methods like rogue Wi-Fi, DNS spoofing, and SSL stripping to insert themselves between you and your destination.
Can on-path attacks be prevented completely?
While no method is 100% foolproof, using encryption, VPNs, MFA, and security-aware behaviour dramatically reduces the risk.
Who are the primary targets?
Anyone can be targeted—but executives, remote workers, and users of unsecured networks are particularly vulnerable.















Leave a comment