The digital battleground is evolving at an unprecedented pace, with Artificial Intelligence (AI) reshaping every facet of conflict. In 2025, the concept of AI Cyberwarfare is no longer theoretical; it’s a stark reality, ushering in an era of new weapons and new rules. Nation-states and sophisticated threat actors are increasingly leveraging AI to launch more potent, elusive, and autonomous cyberattacks, fundamentally altering the landscape of military cyber operations. This shift demands a re-evaluation of our cyber defense strategies, as AI cyber weapons introduce previously unimaginable capabilities and AI-driven cyber threats become the norm. Understanding this paradigm shift is crucial for National cybersecurity and for comprehending the true future of cyber conflict.
Table of Contents
Key Takeaways
- AI Transforms Attack Capabilities: AI empowers attackers with unprecedented speed, scale, and stealth, enabling sophisticated autonomous cyberattacks and making traditional defenses less effective.
- The Rise of AI Cyber Weapons: New classes of AI cyber weapons, including deepfake cyberattacks and self-evolving malware, are emerging, requiring advanced detection and response mechanisms.
- Defense Must Evolve with AI: Effective cyber defense strategies in 2025 rely on leveraging AI for proactive threat hunting, automated incident response, and predictive analytics to counter AI-driven threats.
- Ethical and Regulatory Challenges: The deployment of autonomous AI in military cyber operations raises complex ethical questions and necessitates new international norms and regulations to prevent uncontrolled escalation.
- Human-AI Collaboration is Key: Despite AI’s advancements, human expertise remains vital for strategic decision-making, ethical oversight, and adapting to the dynamic nature of AI Cyberwarfare.
The Dawn of AI Cyberwarfare: Redefining the Digital Battlefield in 2025
The year 2025 finds us at a pivotal juncture where AI’s integration into offensive and defensive cybersecurity has moved beyond mere augmentation to full-scale transformation. We are now firmly in the age of AI Cyberwarfare, a complex domain where algorithms learn, adapt, and execute attacks and defenses with minimal human intervention. This shift has profound implications for military cyber operations, as the speed and scale of potential conflicts increase exponentially.
Consider the traditional cyberattack lifecycle: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. AI injects intelligence and automation into every single one of these stages.
- Automated Reconnaissance: AI can rapidly scan vast networks, identify vulnerabilities, and map attack surfaces far more efficiently than human analysts. It can sift through open-source intelligence (OSINT) and dark web forums to gather actionable insights.
- Dynamic Weaponization: AI can automatically generate highly sophisticated malware variants, polymorphic code that evades signature-based detection, and even custom exploits tailored to specific target environments. This significantly reduces the time from vulnerability discovery to weapon deployment.
- Intelligent Delivery: AI can analyze user behavior and network traffic patterns to determine the optimal delivery mechanism for an attack, whether it’s a meticulously crafted phishing email designed by generative AI or an opportunistic network intrusion.
- Adaptive Exploitation: Once inside a system, AI can autonomously navigate networks, escalate privileges, and identify further targets, dynamically adapting its tactics based on the responses it encounters. This leads to autonomous cyberattacks that are difficult to predict and stop.
The sheer volume of data, the complexity of modern networks, and the speed at which threats emerge necessitate AI-driven solutions on both sides of the conflict. Nations are investing heavily in AI cyber weapons development, recognizing that future geopolitical power will be inextricably linked to superiority in the digital realm. As we look at cyber threats 2024: key incidents and what to expect in 2025 [https://cybertechjournals.com/cyber-threats-2024-key-incidents-and-what-to-expect-in-2025/], the increasing sophistication attributed to AI is undeniable.
This new reality means that the “rules of engagement” are being rewritten. The decision cycle for launching a cyberattack or responding to one can be reduced from hours or days to minutes or even seconds. This speed challenges traditional command and control structures and raises critical questions about human oversight in fully autonomous cyberattacks.
AI in cyberwarfare is not just an amplifier; it’s a game-changer. It shifts the equilibrium, making defense exponentially harder and offense potentially unstoppable without equally advanced countermeasures.
The Arsenal of Tomorrow: AI Cyber Weapons and Autonomous Threats
The development of AI cyber weapons is rapidly expanding the offensive capabilities of state and non-state actors. These aren’t just faster versions of old tools; they represent a fundamental leap in malicious automation and intelligence. Let’s explore some of the most concerning examples:
Autonomous Malware and Swarm Attacks
Traditional malware relies on pre-programmed instructions. AI-driven cyber threats, however, can deploy autonomous malware that exhibits self-learning and self-evolving capabilities. These intelligent agents can:
- Evade Detection: Continuously modify their code and behavior to bypass signature-based antivirus and intrusion detection systems.
- Adapt to Defenses: Analyze network security responses and adjust their attack vectors in real-time to maintain persistence and achieve objectives.
- Coordinate Swarm Attacks: Operate as a decentralized network of malicious bots, each making independent decisions to overwhelm defenses or achieve distributed objectives. Imagine thousands of AI agents simultaneously probing, exploiting, and propagating across a global network.
Deepfake Cyberattacks and Disinformation Campaigns
One of the most insidious AI cyber weapons is the deepfake. While often associated with video manipulation, deepfake technology extends to audio and text, creating hyper-realistic synthetic media that is indistinguishable from genuine content.
| Deepfake Type | Description | Potential Cyberwarfare Impact |
|---|---|---|
| Audio Deepfakes | Replicating voices to impersonate officials or create false directives. | Social engineering, insider threat, stock market manipulation |
| Video Deepfakes | Fabricating footage of leaders or events to spread misinformation. | Destabilization, political interference, propaganda |
| Text Deepfakes | Generating human-like text to create convincing phishing emails or fake news articles. | Advanced phishing, reputation damage, narrative control |
These deepfake cyberattacks can be leveraged in sophisticated influence operations, aiming to sow discord, erode trust, or manipulate public opinion. For example, a deepfake audio recording of a government official issuing a false command could trigger panic or critical infrastructure disruption. Identifying and mitigating these threats is a significant challenge for National cybersecurity in 2025.
AI-Powered Zero-Day Exploitation
Zero-day vulnerabilities are highly prized by attackers because they are unknown to defenders and thus have no patch. AI is revolutionizing their discovery and exploitation:
- Automated Vulnerability Research: AI algorithms can analyze vast amounts of code, identify complex logic flaws, and predict potential zero-day vulnerabilities far quicker than human researchers.
- Exploit Generation: Once a vulnerability is found, AI can automatically generate functional exploits, bypassing the need for manual, time-consuming exploit development.
- Targeted Delivery: AI can then precisely deliver these exploits, observing system responses and refining its approach until the exploit is successful.
This capability drastically reduces the “shelf life” of zero-day vulnerabilities, meaning defenses must become more proactive and predictive. Learn more about AI impact on the CISO role in 2025.
Countering the Threat: Advanced Cyber Defense Strategies
The emergence of AI Cyberwarfare necessitates a new generation of cyber defense strategies. Traditional perimeter defenses and reactive measures are increasingly insufficient against AI-driven cyber threats. In 2025, defense must also embrace AI.
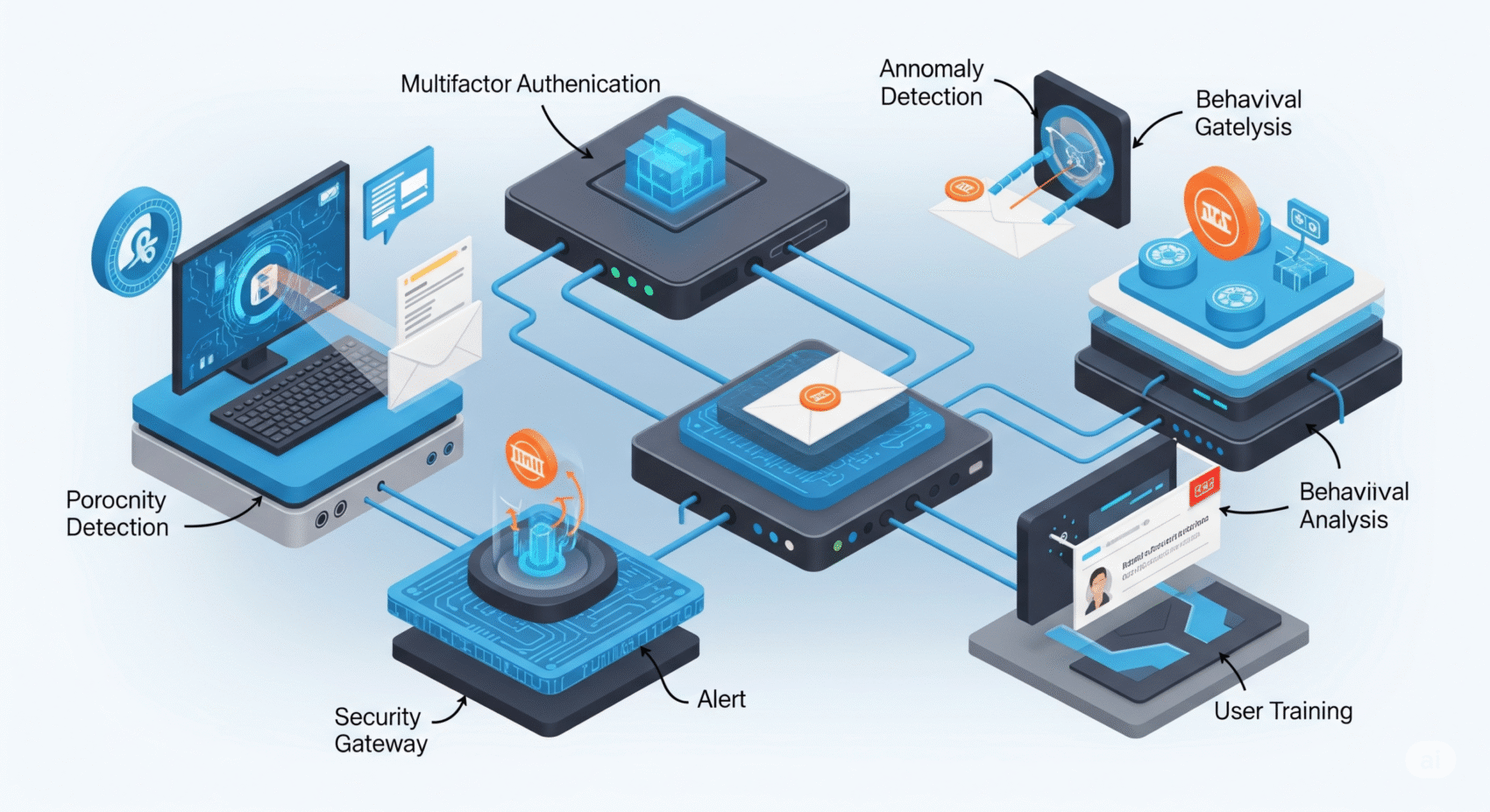
AI-Powered Threat Detection and Response
AI is critical for detecting the subtle, adaptive, and high-speed attacks launched by adversaries leveraging AI.
- Behavioral Analytics: AI systems can establish baseline normal network and user behavior. Deviations from this baseline, even subtle ones, can signal an intrusion. This is far more effective against polymorphic malware than signature-based methods.
- Predictive Threat Intelligence: AI can analyze global threat data, identify emerging attack patterns, and predict where and how the next attacks might occur. This allows organizations to proactively bolster defenses before an attack materializes. You can learn more about AI threat detection tools that actually work.
- Automated Incident Response: When a threat is detected, AI can initiate automated responses, such as isolating compromised systems, blocking malicious IP addresses, or rolling back configurations, drastically reducing the dwell time of attackers. This capability is crucial for responding to rapid autonomous cyberattacks. Explore automated cybersecurity incident response.
- Deception Technologies: AI can be used to create sophisticated honeypots and deception networks that mimic real infrastructure, luring attackers into controlled environments where their tactics, techniques, and procedures (TTPs) can be observed and analyzed without risk to production systems.
Enhancing National Cybersecurity Posture
For nations, the challenge is immense. National cybersecurity involves protecting critical infrastructure, government networks, and citizen data.
- Investment in AI R&D: Governments must invest heavily in AI research and development for defensive purposes, ensuring they remain at the forefront of cyber defense technology.
- Public-Private Partnerships: Collaboration between government agencies, private sector cybersecurity firms, and academic institutions is crucial for sharing threat intelligence, developing new technologies, and fostering a skilled workforce.
- Cyber Resilience and Redundancy: Building systems that can withstand and rapidly recover from attacks, rather than solely focusing on prevention, is paramount. This includes implementing robust backup strategies and disaster recovery plans. Discover how to prepare a disaster recovery plan for your business.
- Workforce Development: Training a new generation of cybersecurity professionals who understand AI, machine learning, and advanced analytics is essential. The human element, though augmented by AI, remains indispensable. See career paths in cyber security.
The Future of Cyber Conflict: Ethical Dilemmas and International Cooperation
As we navigate the future of cyber conflict in 2025, profound ethical and strategic questions arise, particularly concerning the deployment of fully autonomous AI cyber weapons.
Ethical Quandaries of Autonomous Cyber Weapons
The idea of machines making independent decisions about targeting and attack execution without human “in the loop” oversight is deeply troubling.
- Accountability: If an autonomous AI system causes widespread damage or civilian harm, who is responsible? The programmer? The commander who authorized its deployment? The AI itself?
- Escalation Control: How can the use of autonomous cyber weapons be controlled to prevent unintended escalation of conflict? A rapid, AI-driven counterattack might be perceived as a disproportionate response, triggering a spiral of retaliatory actions.
- Unintended Consequences: AI systems, while powerful, can be unpredictable. A bug or an unforeseen interaction could lead to catastrophic outcomes that were never intended by human operators.
These concerns highlight the urgent need for international dialogue and the establishment of norms around the development and use of AI in warfare.
The Imperative for International Cooperation
The global nature of cyber threats means that no single nation can tackle AI Cyberwarfare alone. International cooperation is not just desirable; it’s essential.
- Arms Control for AI Cyber Weapons: Just as there are treaties for nuclear and chemical weapons, there’s a growing call for discussions on limiting the proliferation and use of autonomous offensive AI systems.
- Shared Threat Intelligence: Nations must establish robust mechanisms for sharing real-time threat intelligence on AI-driven cyber threats to create a collective defense posture.
- Joint Research and Development: Collaborating on defensive AI technologies can accelerate innovation and create a more resilient global cybersecurity ecosystem.
- Establishing Norms and Rules of Engagement: Developing international agreements on acceptable and unacceptable uses of AI in cyber conflict is crucial to prevent a chaotic free-for-all. This could involve defining “red lines” for autonomous cyberattacks against critical infrastructure or specific types of data.
“The race for AI supremacy in cyberwarfare is a dangerous one. Without a framework for responsible development and international cooperation, we risk ushering in an era of unprecedented digital instability.”
Preparing for What’s Next: A Roadmap for National Cybersecurity
The landscape of Cyberwarfare in the Age of AI demands a proactive and adaptive approach. In 2025, relying on past strategies is a recipe for failure. Here’s a roadmap for bolstering National cybersecurity:
- Invest in Cutting-Edge AI Defense: Prioritize funding and talent for research, development, and deployment of AI-powered defensive tools, including behavioral analytics, predictive threat intelligence, and automated response systems.
- Regularly Assess and Test Defenses: Conduct frequent, sophisticated penetration testing and red team exercises, specifically designed to simulate AI-driven cyber threats and autonomous cyberattacks. These tests should challenge the organization’s ability to detect and respond to novel AI-powered attacks.
- Cultivate a Cyber-Aware Culture: Human error remains a significant vulnerability. Invest in continuous cybersecurity training that emphasizes the unique risks posed by deepfake cyberattacks and advanced social engineering tactics powered by generative AI. Learn about how to train employees on cybersecurity awareness.
- Embrace Zero Trust Principles: Assume breach and implement a zero-trust architecture where every user, device, and application is continuously verified and authenticated, regardless of its location. This limits the lateral movement of AI cyber weapons once they breach initial defenses. Check out 10 strategies to strengthen digital security.
- Foster Human-AI Teaming: Develop strategies that combine the strengths of AI (speed, data processing) with human intelligence (critical thinking, ethical judgment, strategic insight). AI should augment human analysts, not replace them entirely.
- Participate in International Dialogues: Actively engage in multilateral discussions on AI governance, cyber arms control, and the establishment of responsible norms for state behavior in cyberspace.
- Maintain Resilient Infrastructure: Ensure critical infrastructure is designed with redundancy, segmentation, and robust incident response capabilities to minimize the impact of even successful AI Cyberwarfare attacks. This involves continuous monitoring and patching, as outlined in guides like cybersecurity for industrial control systems: best practices, threats in 2025.
The transformation wrought by AI in cyberwarfare is profound and ongoing. It calls for agility, innovation, and a collaborative spirit among nations and organizations.
Conclusion: Cyberwarfare in the Age of AI
The year 2025 marks a definitive transition into an era where AI Cyberwarfare is not merely a theoretical construct but an active domain of geopolitical competition. The deployment of AI cyber weapons and the proliferation of autonomous cyberattacks have fundamentally rewritten the playbook for military cyber operations, demanding a paradigm shift in cyber defense strategies. From the deceptive power of deepfake cyberattacks to the adaptive nature of AI-driven cyber threats, the challenges to National cybersecurity are more complex and urgent than ever.
As we look towards the future of cyber conflict, it’s clear that technological superiority in AI will be a critical determinant of national security. However, this race must be tempered with ethical considerations and a strong commitment to international cooperation. Building robust defenses, fostering a skilled workforce, and actively participating in global efforts to establish norms for AI in warfare are not just options – they are imperatives. By embracing these actionable next steps, we can hope to navigate the treacherous waters of Cyberwarfare in the Age of AI and secure our digital future.











Leave a comment