In the dynamic world of cybersecurity, while we invest heavily in firewalls, encryption, and advanced threat detection systems, a persistent and often underestimated vulnerability remains: the human element. Social engineering, a deceptive tactic that exploits human psychology rather than technical flaws, is increasingly becoming the preferred vector for cybercriminals. Understanding the various types of social engineering attacks, implementing robust strategies for preventing social engineering, and establishing effective social engineering mitigation plans are paramount for any individual or organization in 2025. This comprehensive guide will delve into the intricacies of this pervasive cyber attack human factor, offering insights into phishing and pretexting, advocating for critical employee security awareness, exploring real-world social engineering examples, and outlining crucial steps for social engineering protection and relevant cybersecurity training 2026.
Table of Contents
Key Takeaways
- Social engineering exploits human psychology: Attackers manipulate individuals into divulging confidential information or performing actions that compromise security, bypassing technological defenses.
- Awareness is your first line of defense: Recognizing the signs of common attack types like phishing, pretexting, and deepfakes is crucial for both individuals and organizations.
- Multi-layered security is essential: Combine employee training, strong authentication, technical controls, and strict verification processes for comprehensive protection.
- Rapid response is critical for mitigation: Having a well-defined incident response plan can significantly reduce the damage from a successful social engineering breach.
- The threat is evolving with AI: Future social engineering attacks in 2026 will likely leverage advanced AI for more convincing and scalable deception, demanding continuous adaptation of defenses.
What Is Social Engineering?
The Definition
At its core, social engineering is the art of manipulating people to give up confidential information or perform actions they wouldn’t normally do. It’s not about hacking computers with complex code; it’s about hacking the human mind. Attackers use psychological tricks, often masquerading as trusted entities, to convince victims to willingly provide access, data, or funds. This approach bypasses even the most sophisticated technical security measures, as the vulnerability lies within the human decision-making process.
Why Attackers Use Human Manipulation
The reason attackers gravitate towards human manipulation is simple yet profound: humans are often the weakest link in the security chain. While systems can be patched and firewalls configured, human psychology remains relatively consistent, making it a predictable target. A well-crafted social engineering attack requires minimal technical expertise from the attacker, yet can yield high returns, making it an attractive method for illicit gains. It’s often easier to trick someone into revealing their password than to try and crack it.
Social Engineering vs. Technical Hacking
It’s important to distinguish between social engineering and traditional technical hacking.
- Social Engineering: Focuses on human interaction and psychological manipulation. Examples include tricking an employee into clicking a malicious link or revealing credentials. It exploits trust, curiosity, or fear.
- Technical Hacking: Involves exploiting vulnerabilities in software, hardware, or networks. Examples include exploiting unpatched systems, brute-forcing passwords, or launching DDoS attacks.
While distinct, these two methods are often used in tandem. A social engineering attack might be the initial entry point, leading to the deployment of malware that then leverages technical vulnerabilities. Understanding the cyber attack human factor is crucial because it highlights that even with cutting-edge technology, human vigilance is non-negotiable.
Why Social Engineering Works
Social engineering preys on fundamental human traits and behaviors, making it incredibly effective. Attackers expertly craft scenarios that exploit our natural inclinations.
Trust Exploitation
Humans are generally wired to trust, especially those who appear to be in positions of authority or known contacts. Attackers exploit this by impersonating IT support, senior management, vendors, or even friends and family. A seemingly legitimate email from a “known” source is far more likely to be opened and acted upon than one from an unknown sender.
Emotional Manipulation (Urgency, Fear, Authority)
Emotions are powerful motivators, and social engineers are masters at wielding them.
- Urgency: Creating a false sense of urgency (“Act now or your account will be closed!”) pressures victims into making hasty decisions without proper verification.
- Fear: Threatening consequences (“Your computer is infected, click here to fix it immediately!”) can induce panic, leading individuals to bypass their better judgment.
- Authority: Impersonating someone with authority (“This is the CEO, I need you to transfer funds immediately”) leverages the natural tendency to comply with superiors.
These tactics bypass critical thinking, forcing victims into reactive rather than thoughtful responses.
Lack of Verification
In busy environments, individuals often neglect to verify unusual requests, especially if they appear to come from a trusted source. A quick phone call or a separate email to confirm a request could prevent many social engineering attacks, but often this step is skipped. This highlights why strict verification procedures are key to preventing social engineering.
Overloaded Employees
Modern workplaces often see employees juggling multiple tasks, operating under tight deadlines, and constantly bombarded with information. An overloaded employee is more susceptible to social engineering attacks because they are less likely to notice subtle red flags. They might be quicker to open an email or click a link to clear their inbox or complete a task, inadvertently falling victim to phishing and pretexting. This makes ongoing employee security awareness training even more critical.
Common Types of Social Engineering Attacks
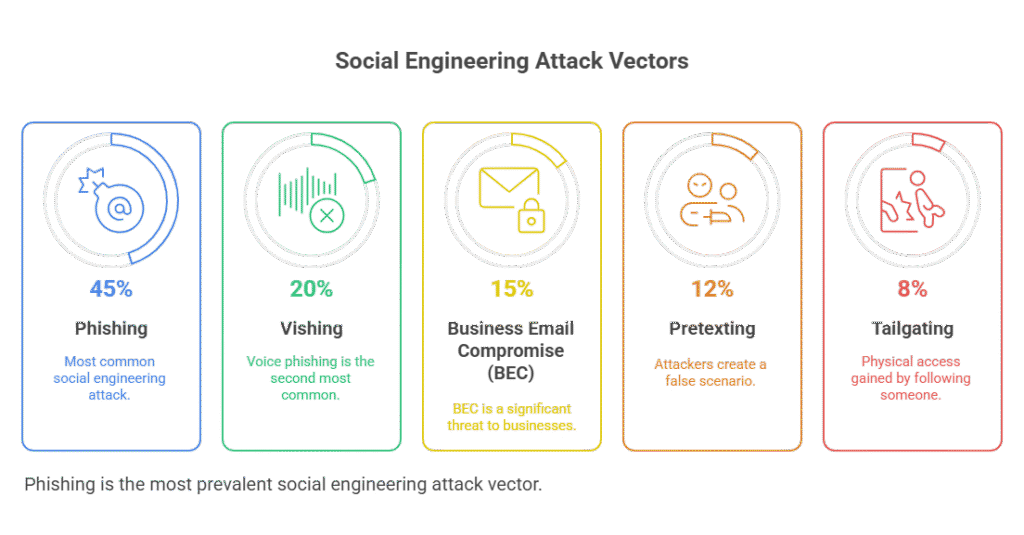
The landscape of social engineering is diverse, with attackers continually refining their techniques. Here, we’ll explore some of the most prevalent types of social engineering attacks.
Phishing (Email-Based Attacks)
Phishing is arguably the most common type of social engineering attack. It involves sending fraudulent emails that appear to come from a reputable source, such as a bank, a popular online service, or a government agency. The goal is to trick the recipient into clicking a malicious link (which leads to a fake login page or downloads malware) or opening an infected attachment. These emails often contain generic greetings and play on fear or urgency. Learn more about identifying phishing emails by understanding the differences between spam vs. phishing.
Spear Phishing & Whaling
These are more targeted forms of phishing:
- Spear Phishing: Instead of generic emails, spear phishing attacks are tailored to specific individuals or organizations. Attackers conduct research to gather personal information (job title, interests, recent activities) to make the email appear highly legitimate and relevant to the target.
- Whaling: A highly specific form of spear phishing that targets high-profile individuals within an organization, such as CEOs, CFOs, or other senior executives. The aim is often to gain access to sensitive corporate data or initiate large financial transfers. This tactic is part of sophisticated cyber attack human factor strategies.
Smishing & Vishing
Beyond email, social engineering extends to other communication channels:
- Smishing (SMS Phishing): Involves sending malicious text messages. These often contain links to fake websites or prompt the victim to call a fraudulent number.
- Vishing (Voice Phishing): Uses phone calls to trick victims. Attackers might impersonate banks, tech support, or government officials to extract personal information or financial details. They often use VoIP technology to spoof caller IDs, making calls appear legitimate.
Pretexting
Pretexting involves creating a believable, fabricated scenario (a “pretext”) to engage a target and gather information. Unlike phishing, which relies on a quick click, pretexting is often a more extended conversation. The attacker might pretend to be a surveyor, a new employee, or an auditor who “needs” certain information to complete a task. The goal is to build trust and manipulate the victim into revealing sensitive data. This is a highly effective method used by sophisticated attackers for phishing and pretexting.
Baiting & USB Drops
- Baiting: Attackers leave malware-infected devices (like USB drives) in public places, hoping a curious victim will pick them up, insert them into their computer, and unknowingly infect their system. The device might be labeled intriguingly, like “Confidential Payroll Data 2025.”
- USB Drops: A variation where USB drives are intentionally left in locations near the target organization, often labeled with enticing titles to encourage employees to plug them in.
Tailgating & Impersonation
These are physical social engineering tactics:
- Tailgating: An unauthorized person follows an authorized person into a restricted area. They might pretend to be a delivery person, a new employee, or simply someone who “forgot their badge,” relying on the target’s politeness to hold the door open.
- Impersonation: An attacker pretends to be someone they are not to gain physical access, information, or trust. This could involve dressing like a maintenance worker or a high-ranking executive.
Business Email Compromise (BEC)
BEC attacks are a sophisticated form of spear phishing where attackers impersonate a high-level executive (like a CEO or CFO) and send emails to employees (often in finance) requesting urgent wire transfers or sensitive data. These emails are highly convincing and often result in significant financial losses. BEC is a major concern for social engineering mitigation in enterprises.
Deepfake Social Engineering
Emerging as a significant threat, deepfake social engineering leverages AI to create highly realistic fake audio or video. Attackers can use deepfake technology to impersonate executives or trusted individuals, making highly convincing vishing calls or video conferences that request sensitive information or authorize fraudulent transactions. This advanced technique represents a new frontier in the cyber attack human factor.
Real-World Examples of Social Engineering Attacks
Examining past incidents helps underscore the pervasive threat of social engineering and the critical need for social engineering protection.
2023–2025 Enterprise Cases
Over the past few years, we’ve seen a surge in sophisticated social engineering attacks targeting enterprises. Many of these involved highly customized spear phishing campaigns that bypassed traditional email filters. For instance, a major tech company reported a breach in late 2024 where employees were tricked into providing their multi-factor authentication (MFA) codes through a meticulously crafted phishing site that mimicked the company’s internal portal. Attackers leveraged publicly available employee information to personalize their outreach, making the emails incredibly believable [1]. This highlights the need for continuous employee security awareness training.
Deepfake CFO Attack
One of the most alarming examples occurred in 2023, where a UK-based energy firm’s CEO was reportedly tricked into transferring €220,000 to a fraudulent account after receiving a deepfake audio call. The attacker used AI-generated voice technology to perfectly imitate the voice and intonation of the parent company’s German CEO, requesting an urgent transfer [2]. This incident perfectly illustrates the growing threat of deepfake social engineering and the evolution of the cyber attack human factor.
IT Support Impersonation
A classic and still highly effective social engineering tactic is IT support impersonation. In early 2025, several university employees fell victim to vishing calls where attackers, posing as IT help desk staff, claimed there was a “critical security update” or “account lockout.” They then persuaded employees to install “remote access software” (which was actually malware) or provide their login credentials directly. These attacks often exploit the immediate need for technical assistance, demonstrating why strong verification procedures are vital for preventing social engineering.
How to Prevent Social Engineering in Organizations
Preventing social engineering requires a multi-faceted approach that addresses both the human and technical aspects of security. No single solution offers complete social engineering protection.
Employee Security Awareness Training
This is the cornerstone of any effective social engineering prevention strategy. Regular, engaging, and updated employee security awareness training is crucial. Training should:
- Educate on common attack types: Detail types of social engineering attacks like phishing, pretexting, smishing, and deepfakes.
- Provide practical examples: Use real-world social engineering examples relevant to the organization.
- Teach detection skills: Help employees recognize red flags such as suspicious links, unusual requests, or pressure tactics.
- Encourage reporting: Establish clear channels for employees to report suspicious emails or calls without fear of reprimand.
- Phishing simulations: Conduct regular simulated phishing exercises to test employee vigilance and reinforce learning. These should be part of a comprehensive cybersecurity training 2026 program.
Strong MFA and Authentication Controls
Implementing multi-factor authentication (MFA) across all systems significantly enhances security. Even if an attacker manages to obtain a password through social engineering, MFA acts as a crucial barrier. Organizations should also consider adaptive authentication, which requires additional verification steps for unusual login attempts. For more on strengthening digital security, refer to 10 strategies to strengthen digital security.
Email & Endpoint Security Tools
Technical controls play a vital role in reducing the volume of social engineering attempts that reach employees.
- Email filters: Advanced email security gateways can detect and block malicious emails, including phishing attempts, before they land in an employee’s inbox.
- Antivirus/Antimalware: Endpoint detection and response (EDR) solutions can identify and quarantine malicious files that might be downloaded as part of a social engineering attack.
- URL filtering: Web filters can block access to known malicious websites, even if an employee accidentally clicks a phishing link.
- DLP (Data Loss Prevention): Tools that prevent sensitive information from being exfiltrated from the organization, even if an employee is tricked into providing access. Learn more about data loss prevention.
Zero Trust Policies
Adopting a Zero Trust security model means “never trust, always verify.” This approach assumes that no user, device, or application should be automatically trusted, regardless of whether they are inside or outside the network. Every access request is rigorously authenticated and authorized. This drastically reduces the impact of a compromised credential obtained through social engineering, as even authenticated users would have limited access based on their specific needs.
Strict Verification Procedures
Establish clear protocols for verifying requests for sensitive information or actions, especially financial transactions.
- Out-of-band verification: For financial transfers or changes to sensitive data, always verify the request through a separate communication channel (e.g., a phone call to a known, pre-established number, not one provided in the suspicious email).
- Two-person rule: For high-value transactions, require approval from two different individuals.
- Questioning unusual requests: Empower employees to question and escalate any request that seems out of the ordinary, regardless of who it appears to come from.
Least Privilege Access Controls
Implement the principle of least privilege, meaning users are granted only the minimum access rights necessary to perform their job functions. This limits the damage an attacker can do even if they successfully compromise an employee’s account through social engineering. For example, a marketing employee should not have access to financial systems.
How to Detect Social Engineering Attempts
Vigilance is key to social engineering protection. Knowing what to look for can turn an unsuspecting target into a resilient defender against the cyber attack human factor.
Suspicious Language (Urgency, Threats)
Be wary of any communication that attempts to pressure you into immediate action. Attackers often use phrases like:
- “Urgent action required!”
- “Your account will be suspended if you don’t respond immediately.”
- “Failure to comply will result in penalties.”
- “Confidential: Do not share this email.”
These are designed to bypass critical thinking and force a quick, unverified response.
Unexpected Attachment or Link
Even if an email appears to come from a known sender, question unexpected attachments or links.
- Hover over links: Before clicking, hover your mouse over the link to see the actual URL. Does it match the sender’s legitimate domain? Look for subtle misspellings (e.g.,
amazon.co-minstead ofamazon.com). - Unusual file types: Be suspicious of unexpected file types, especially executables (.exe), script files (.js, .vbs), or compressed archives (.zip) in an email that doesn’t clearly require them.
- Out-of-context requests: Did you expect this attachment? Does the sender usually send files like this?
Credential, OTP, or Payment Request
Legitimate organizations rarely ask for your password, one-time passcodes (OTPs), or credit card details directly via email or unsolicited phone calls.
- Never share passwords: Your password should only be entered on official, verified websites.
- Guard your OTPs: OTPs are designed for single use verification; never give them to someone over the phone or enter them on an unverified site.
- Verify payment requests: Always use out-of-band verification for any request involving financial transactions. This is crucial for social engineering mitigation.
Mismatched Sender Email
This is one of the clearest red flags in email-based social engineering.
- Check the full sender address: Don’t just look at the display name (e.g., “CEO John Smith”). Click to expand the sender’s full email address. Does it match the company’s official domain? (e.g.,
ceo@company.comvs.ceo.company@outlook.com). - Look for subtle misspellings: Attackers often register domains that look very similar to legitimate ones (e.g.,
companyy.comorc0mpany.com).
Verification Red Flags
When dealing with phone calls or in-person interactions, look for these:
- Unwillingness to provide details: If someone claiming to be from IT or a vendor refuses to provide their employee ID, a callback number, or specific details that verify their identity, be suspicious.
- Pressure to act immediately: Any attempt to rush you and prevent you from verifying their identity or the request is a major red flag.
- Request for unusual access: Be cautious if someone asks for remote access to your computer or to install software without prior arrangement.
By actively looking for these indicators, individuals become the frontline defense against all types of social engineering attacks.
How to Mitigate a Social Engineering Breach
Even with the best preventive measures, a social engineering attack can sometimes succeed. Having a robust incident response plan for social engineering mitigation is crucial to minimize damage and recover quickly. This is where your organization’s automated cybersecurity incident response capabilities become invaluable.
Steps to Isolate Systems
The immediate priority is to contain the breach.
- Disconnect affected devices: If a device is suspected of being compromised, immediately disconnect it from the network (unplug the ethernet cable, disable Wi-Fi) to prevent malware spread or further data exfiltration.
- Disable compromised accounts: If an employee’s credentials were stolen, disable their account immediately to cut off attacker access.
- Block malicious IPs/URLs: Update firewalls and security tools to block any IP addresses or URLs identified as part of the attack.
Password Resets & MFA Review
- Force password resets: Require immediate password resets for all potentially compromised accounts. Consider a company-wide password reset if the scope of the breach is unclear.
- Review MFA configurations: Ensure MFA is robustly implemented and that attackers haven’t found a way to bypass it. Re-enroll users in MFA if necessary.
Incident Response Team Involvement
Engage your dedicated incident response team (or external cybersecurity experts) as soon as a breach is detected. They are equipped to:
- Coordinate the response: Lead the efforts to contain, eradicate, and recover from the attack.
- Communicate effectively: Manage internal and external communications, including potential notification requirements.
- Document the incident: Keep detailed records of all actions taken, findings, and lessons learned. For smaller businesses, understanding how to prepare for a cyber attack is key.
Forensic Investigation
A thorough forensic investigation is essential to understand the scope and impact of the breach.
- Identify the entry point: Determine how the social engineering attack succeeded.
- Assess data compromise: Identify what data was accessed or exfiltrated.
- Determine attacker activities: Understand what the attacker did once inside the network.
- Legal & compliance reporting: Gather evidence for potential legal action or regulatory reporting, especially concerning data privacy regulations like GDPR or CCPA.
User Re-training
After a breach, it’s vital to reinforce employee security awareness.
- Post-incident briefing: Conduct a mandatory briefing for all employees, explaining what happened, how it was mitigated, and emphasizing the lessons learned.
- Targeted training: Provide additional, specialized training to individuals or departments that were specifically targeted or affected by the social engineering incident.
Strengthening Security Controls
The incident provides valuable insights to strengthen your overall social engineering protection.
- Patch vulnerabilities: Address any technical vulnerabilities discovered during the investigation.
- Enhance email security: Upgrade email filters, implement DMARC, DKIM, and SPF records more rigorously.
- Review access policies: Re-evaluate and tighten least privilege access controls.
- Update incident response plan: Refine the incident response plan based on the experience gained.
- Consider new technologies: Explore advanced threat intelligence or AI-driven security solutions that could detect similar attacks in the future.
Future of Social Engineering in 2026
As technology advances, so too do the methods of cybercriminals. The future of social engineering in 2026 promises even greater sophistication, making continuous adaptation of cybersecurity training 2026 and defenses absolutely critical.
Impact of AI-Generated Attacks
Artificial intelligence will revolutionize social engineering, making attacks more personalized, scalable, and convincing.
- Hyper-realistic phishing content: AI can generate grammatically perfect, contextually relevant phishing emails that are almost indistinguishable from legitimate communications. It can analyze public data to craft emails tailored to individual targets, dramatically improving their success rates.
- Automated spear phishing: AI tools will enable attackers to automate the research and crafting of spear phishing campaigns, allowing them to target thousands of individuals with highly personalized messages simultaneously. This will significantly increase the volume and effectiveness of phishing and pretexting at scale.
Evolution of Deepfake Social Engineering
Deepfake technology will continue to mature, posing a significant challenge to verification processes.
- Convincing deepfake audio/video calls: AI will make it easier and cheaper to generate real-time deepfake audio and video. This means attackers could convincingly impersonate executives or colleagues during live video calls, making requests for sensitive information or financial transfers incredibly difficult to discern as fraudulent.
- Synthetic identities: Attackers could leverage AI to create entire fake personas with realistic backstories, social media profiles, and even deepfake voice/video, making pretexting attacks far more robust and harder to expose.
Automated Phishing-as-a-Service
The dark web already offers phishing kits, but 2026 will likely see the rise of more sophisticated “phishing-as-a-service” platforms. These platforms, powered by AI, will provide aspiring attackers with easy-to-use tools to launch highly effective social engineering campaigns, including advanced customization, automated targeting, and built-in evasion techniques. This lowers the bar for entry into cybercrime, making social engineering examples more frequent and widespread.
Greater Need for Human-Factor Security
Paradoxically, as technology makes social engineering more sophisticated, the focus on the cyber attack human factor will become even more pronounced. Technical defenses will improve, but the human element will remain the primary vulnerability. This necessitates:
- Advanced cognitive training: Moving beyond basic awareness to training that helps individuals develop critical thinking skills, question assumptions, and identify subtle psychological manipulation tactics.
- Behavioral analytics: Using AI to monitor user behavior for anomalies that might indicate a social engineering attempt or compromise, such as unusual login times or data access patterns.
- Continuous adaptive security awareness: Regular, updated, and context-specific training that evolves with the threat landscape, rather than generic annual refreshers. This is the essence of effective cybersecurity training 2026.
Conclusion
In the ever-evolving landscape of cyber threats in 2025 and beyond, social engineering stands as a formidable adversary, reminding us that the human element remains the most significant and often exploited vulnerability. As we’ve explored the diverse types of social engineering attacks, from the ubiquitous phishing and pretexting to the emerging threat of deepfakes, it’s clear that technological safeguards alone are insufficient.
True social engineering protection hinges on a comprehensive strategy. This strategy must integrate robust technical controls like strong MFA, advanced email security, and Zero Trust policies with an unwavering commitment to employee security awareness and continuous cybersecurity training 2026. Organizations must foster a culture where questioning suspicious requests is encouraged, and where a well-defined incident response plan for social engineering mitigation is not just a document, but a practiced reality.
The future, particularly in 2026, will bring AI-powered attacks that are more convincing and scalable than ever before. This demands that we not only understand these threats but proactively prepare for them by investing in our people – enhancing their vigilance, critical thinking, and their ability to be the strongest link in our digital defenses. Human behavior remains the weakest link in cybersecurity. With the right mix of awareness, tools, and policies, organizations can greatly reduce social engineering risks.
Actionable Next Steps for Organizations:
- Assess Your Current Vulnerabilities: Conduct regular social engineering penetration tests and phishing simulations to identify weaknesses in your human and technical defenses.
- Invest in Ongoing Training: Implement continuous, engaging, and updated employee security awareness programs covering all types of social engineering attacks, including the latest AI-driven threats.
- Strengthen Technical Controls: Ensure robust email filtering, endpoint detection, MFA across all systems, and consider implementing Zero Trust architecture.
- Develop & Practice Incident Response: Create a clear, actionable plan for detecting, containing, and recovering from social engineering breaches, and conduct regular tabletop exercises.
- Foster a Culture of Skepticism: Empower employees to question unusual requests and report anything suspicious without fear of reprisal.
By prioritizing these steps, we can transform the human factor from a vulnerability into an organization’s most resilient defense against social engineering.
Frequently Asked Questions (FAQs) About Social Engineering
1. What is social engineering, and why should I care?
- Answer: Social engineering is the manipulation of individuals into divulging sensitive information or performing actions that compromise security. It’s a leading cause of data breaches, making awareness crucial. Learn more here .
2. How do attackers use AI in social engineering?
- Answer: Attackers leverage AI to create deepfakes, craft personalized phishing emails, and automate social engineering campaigns. For details, visit IBM’s AI in Cybersecurity .
3. Can social engineering occur in non-digital environments?
- Answer: Yes, examples include tailgating (unauthorized physical access) and pretexting calls. Physical security measures are essential to mitigate these risks. Explore CISA’s Physical Security Guide .
4. How can small businesses protect themselves from social engineering?
- Answer: Small businesses can adopt free or low-cost solutions like Google Workspace Security or Microsoft Defender for Business , enforce strong password policies, and provide regular training. Find resources here .
5. What are the ethical considerations when simulating phishing attacks?
- Answer: Simulated phishing campaigns must balance effectiveness with respect for employee privacy and morale. Focus on education rather than blame. Refer to KnowBe4’s Best Practices .
6. How can gamification improve social engineering awareness?
- Answer: Gamification makes learning fun and memorable. Platforms like KnowBe4 use quizzes, leaderboards, and rewards to engage employees. Learn more here .
7. What are the limitations of traditional security measures in addressing social engineering?
- Answer: Traditional measures like firewalls and antivirus software focus on technical vulnerabilities and often overlook human behavior. Specialized tools like email filtering and user behavior analytics are needed. Explore Proofpoint’s Email Security .
8. How does organizational hierarchy influence social engineering risks?
- Answer: Higher-level employees, such as executives or IT administrators, pose greater risks due to elevated access privileges. Implement separation of duties and regularly audit privileged accounts. See NIST’s Access Control Guidelines .
9. What role does employee offboarding play in mitigating social engineering?
- Answer: Failing to revoke access privileges during offboarding leaves the door open for social engineering attacks. Establish standardized processes for disabling accounts and retrieving company property. For guidance, visit CISA’s Offboarding Checklist .
10. What are some real-world examples of social engineering in different industries?
- Answer: Examples include healthcare (patient record theft), finance (executive impersonation scams), and technology (proprietary code theft). These cases highlight the importance of industry-specific defenses. Explore Verizon’s DBIR for case studies.















Leave a comment