In 2025, the digital landscape is more interconnected and perilous than ever. Organizations face an unrelenting barrage of sophisticated cyberattacks, making a robust cybersecurity policy not just a best practice, but a critical imperative for survival and growth. Without a well-defined information security policy and a clear information security framework, businesses are essentially navigating a minefield blindfolded. This comprehensive guide is designed for Chief Information Security Officers (CISOs), Chief Technology Officers (CTOs), and Chief Information Officers (CIOs) who are tasked with establishing strong cyber security governance and protecting their enterprise from evolving threats. We will walk through the essential steps to implement an information security policy, offering insights akin to a cyber security policy template for enterprises, and providing a cyber risk management checklist to ensure comprehensive coverage.
Table of Contents
Key Takeaways
- A robust cybersecurity policy is a strategic board-level priority, directly impacting business continuity and regulatory compliance in 2025.
- Understanding your organization’s unique business context, critical assets, and regulatory obligations, especially in India, is foundational to policy development.
- Effective cyber security governance requires clear roles, responsibilities (RACI), and a cross-functional approach to policy ownership and enforcement.
- Policies must be risk-based, leveraging recognized control frameworks (e.g., ISO 27001, NIST CSF) and addressing core domains like access control, data protection, and cloud security.
- Continuous improvement, driven by metrics, audits, and security awareness programs, is vital for maintaining an adaptive and resilient information security framework.
Why a Robust Cybersecurity Policy is Non-Negotiable
The modern enterprise operates in a constant state of digital transformation. Cloud adoption, remote work, IoT devices, and increasingly complex supply chains have broadened the attack surface dramatically. Simultaneously, cybercriminals are evolving their tactics, employing sophisticated ransomware, phishing campaigns, and supply chain attacks that can cripple organizations.
Beyond the immediate threat of attack, regulatory expectations are intensifying globally and locally. Governments are enacting stringent data protection laws that impose significant penalties for non-compliance. In India, for instance, the Digital Personal Data Protection Act (DPDPA) 2023 sets high standards for data handling, mandating robust security measures and swift breach notifications. For these reasons, a well-documented and actively enforced cybersecurity policy has transitioned from an IT concern to a board-level priority.
Link Cyber Risk to Business Impact
The absence or inadequacy of a robust information security policy directly translates into tangible business risks:
- Downtime and Operational Disruption: A successful ransomware attack or data breach can halt operations, leading to significant revenue loss and customer dissatisfaction.
- Financial Loss: Beyond direct ransomware payments, organizations face costs related to incident response, forensic investigations, data recovery, legal fees, and regulatory fines.
- Legal Exposure and Regulatory Penalties: Non-compliance with data protection laws (like DPDPA 2023) can result in hefty fines, legal action from affected individuals, and mandatory reporting obligations that damage public trust.
- Reputational Damage: News of a data breach erodes customer confidence, harms brand image, and can lead to a long-term loss of market share. In today’s interconnected world, reputation can be more valuable than any physical asset.
A strategic cybersecurity policy serves as the blueprint for mitigating these risks, demonstrating due diligence, and ensuring resilience in the face of adversity. It is foundational to effective cyber risk management.
Understand Your Business and Regulatory Context in India
Before drafting a single clause of your cybersecurity policy, you must gain a deep understanding of your organization’s operational landscape and the specific regulatory environment it operates within. This foundational step is crucial for tailoring an information security framework that is both effective and compliant.
Map Critical Assets and Data Flows:
- Identify Crown Jewels: What are your most valuable assets? This includes intellectual property, customer data, financial records, core applications, and critical infrastructure.
- Data Flow Analysis: Where does sensitive data reside? How is it created, processed, stored, and transmitted? Document data flows across on-premise systems, cloud environments (IaaS, PaaS, SaaS), Operational Technology (OT), Internet of Things (IoT) devices, and third-party integrations. This mapping helps identify potential vulnerabilities and exposure points.
- Business Processes: Understand the key business processes that rely on these assets and data. This context helps prioritize security controls based on their impact on operations.
Summarize Key Indian and Sectoral Obligations:
India’s regulatory landscape for cybersecurity is evolving rapidly. Your cybersecurity policy must reflect these specific obligations. Key elements include:
- Digital Personal Data Protection Act (DPDPA) 2023: This landmark legislation governs the processing of digital personal data in India. It mandates consent, data minimization, accuracy, purpose limitation, storage limitation, reasonable security safeguards, and accountability. Your policy must detail how data fiduciaries (organizations) and data processors will adhere to these principles, including robust data breach notification procedures.
- CERT-In Directions: The Indian Computer Emergency Response Team (CERT-In) issues directives under the Information Technology (IT) Act, 2000. Their directions, particularly regarding incident reporting, log retention, and vulnerability management, are critical. For example, the 2022 CERT-In directions on cyber incident reporting require service providers, intermediaries, data centers, and corporate bodies to report cyber incidents within six hours of being aware of them.
Sector-Specific Guidelines:
- Reserve Bank of India (RBI): For financial institutions, RBI guidelines (e.g., on Cyber Security Framework for Banks, guidelines on Information and Cyber Security for NBFCs) dictate extensive requirements for data encryption, network security, incident response, and third-party risk management.
- Securities and Exchange Board of India (SEBI): Capital market entities must comply with SEBI’s cybersecurity frameworks, covering aspects like data backup, disaster recovery, and protection against unauthorized access.
- Insurance Regulatory and Development Authority of India (IRDAI): The insurance sector has its own guidelines for information and cybersecurity, emphasizing data privacy, system integrity, and business continuity.
- Other Regulators: Depending on your industry (e.g., healthcare, telecommunications), other sector-specific bodies may impose additional cybersecurity mandates.
By meticulously analyzing these internal and external factors, you lay the groundwork for a robust information security policy that is both practical and legally sound. This answers the crucial question of how to create a cybersecurity policy that is contextually relevant.
Define Governance, Roles, and Ownership
Effective cyber security governance is the backbone of any robust information security framework. Without clear accountability and a defined structure, even the best-intentioned policies will fail. This section focuses on establishing the organizational components necessary to manage, approve, and enforce your cybersecurity policy.
Describe the Governance Structure
A multi-tiered governance structure ensures that cybersecurity is viewed as an enterprise-wide responsibility, not just an IT problem.
- Board Oversight: The Board of Directors holds ultimate accountability for the organization’s risk posture. They must receive regular, high-level reports on cyber risks, policy effectiveness, and major incidents. Their role is to provide strategic direction, approve significant cybersecurity investments, and ensure the cybersecurity policy aligns with business objectives and risk appetite.
- Risk Committee: Often a sub-committee of the Board or a separate executive committee, this body provides a more detailed review of risk assessments, mitigation strategies, and policy adherence. They act as an intermediary, translating technical risks into business implications for the Board.
- CISO Mandate: The Chief Information Security Officer (CISO) is the central figure responsible for developing, implementing, and overseeing the information security policy. The CISO reports directly to senior leadership (e.g., CEO, CIO, or Board), ensuring sufficient authority and visibility. Their mandate includes establishing the information security framework, managing the security team, and fostering a security-aware culture.
- Cross-Functional Security Council: This committee, comprising representatives from IT, Legal, HR, Business Units, and other relevant departments, meets regularly to discuss security issues, review policy effectiveness, and ensure alignment across the organization. This council is crucial for ensuring the cybersecurity policy is practical and understood by all stakeholders.
Clarify RACI for Policy Ownership, Approval, Periodic Reviews, and Exception Management
A clear RACI (Responsible, Accountable, Consulted, Informed) matrix is indispensable for defining roles and responsibilities related to the cybersecurity policy.
| Role/Department | Responsible (Does the work) | Accountable (Ultimately in charge) | Consulted (Provides input) | Informed (Kept updated) |
|---|---|---|---|---|
| Policy Development | CISO & Security Team | CISO | IT, Legal, HR, Business Units | Board, Risk Committee |
| Policy Approval | CISO & Risk Committee | Board | Legal, Business Unit Heads | All Employees |
| Policy Enforcement | Department Heads, IT, CISO | CISO | Security Team | All Employees |
| Periodic Reviews | CISO & Security Team | CISO | Internal Audit, Legal, Key Business Stakeholders | Board, Risk Committee |
| Exception Mgmt. | CISO, Department Head | CISO | Legal, Risk Committee (for significant exceptions) | Board (for major exceptions), Internal Audit |
| Security Awareness | HR, CISO & Security Team | CISO | All Department Heads | All Employees |
- Policy Ownership: The CISO and their security team are typically responsible for drafting and maintaining the core cybersecurity policy. However, specific sub-policies (e.g., HR security policy) might be owned by respective department heads, with the CISO providing oversight and ensuring integration into the overall information security framework.
- Approval: Formal approval of the overarching information security policy should rest with the Board or a delegated Risk Committee, underscoring its strategic importance.
- Periodic Reviews: Policies are living documents. Regular reviews (at least annually, or more frequently in response to significant changes in threat landscape, technology, or regulations) are critical to ensure the cybersecurity policy remains relevant and effective. The CISO, with input from the Security Council, should lead these reviews.
- Exception Management: No policy can cover every scenario. A clear process for requesting, evaluating, and approving exceptions to the cybersecurity policy is essential. This process should involve risk assessment, documented justifications, time limits for exceptions, and appropriate approval levels (e.g., CISO for minor exceptions, Risk Committee for major ones).
This well-defined governance structure is a fundamental step in how to create a cybersecurity policy that is not just written, but actively practiced and embedded within the organizational culture.
Build Risk-Based Policy Foundations
A truly effective cybersecurity policy isn’t a generic document; it’s a strategic tool built upon a thorough understanding of an organization’s unique risk profile. This section emphasizes the critical role of risk assessment and the strategic use of control frameworks in building a robust information security framework.
Perform a Risk Assessment and Connect Policy Requirements to Top Business Risks
The starting point for any robust cybersecurity policy is a comprehensive cyber risk assessment. This process identifies, analyzes, and evaluates potential cyber threats and their impact on your organization.
Steps for a Risk Assessment:
- Asset Identification: Identify all critical information assets (hardware, software, data, services, people).
- Threat Identification: List potential threats to these assets (e.g., ransomware, insider threats, phishing, DDoS, data exfiltration, cloud misconfigurations, supply chain attacks).
- Vulnerability Identification: Identify weaknesses in your systems, processes, or people that could be exploited by threats.
- Impact Analysis: Determine the business impact if a threat exploits a vulnerability (e.g., financial loss, reputational damage, operational disruption, legal penalties).
- Likelihood Assessment: Estimate the probability of each threat occurring.
- Risk Calculation: Combine impact and likelihood to determine the overall risk level.
- Risk Prioritization: Rank risks based on their severity.
Once risks are identified and prioritized, your cybersecurity policy must directly address the top business risks. For example:
Ransomware: Policy clauses should mandate regular backups (offline and immutable), robust endpoint detection and response (EDR/XDR) solutions, user awareness training (phishing prevention), strong access controls, and a well-tested incident response plan specifically for ransomware.
Data Exfiltration: Policy requirements should include data classification, encryption at rest and in transit, data loss prevention (DLP) technologies, strict access controls (least privilege), and comprehensive logging and monitoring.
Insider Threats: Policies must cover background checks, segregation of duties, privileged access management (PAM), user behavior analytics (UBA), and clear disciplinary actions for policy violations.
Cloud Misconfigurations: The cybersecurity policy needs specific sections detailing secure configuration baselines for cloud environments, continuous monitoring of cloud resources, and adherence to the shared responsibility model.
This risk-based approach ensures that your information security policy is tailored, efficient, and directly contributes to reducing the organization’s overall cyber risk exposure. It provides a practical answer to how to create a cybersecurity policy that is truly impactful.
Use a Recognized Control Framework Baseline
While your policy must be tailored, you don’t need to start from scratch. Leveraging established information security framework baselines provides a structured approach and ensures comprehensive coverage. You can then tune these frameworks to your organization’s specific risk appetite and regulatory context.
Commonly used frameworks include:
- ISO/IEC 27001: An international standard for Information Security Management Systems (ISMS). It provides a systematic approach to managing sensitive company information so that it remains secure. It includes a comprehensive set of controls (Annex A) covering various aspects of information security.
- NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology, the CSF provides a flexible framework to reduce cyber risks. It’s structured around five core functions: Identify, Protect, Detect, Respond, and Recover. Many organizations use the CSF to assess and improve their cybersecurity posture.
- Sectoral Circulars/Guidelines: As discussed, Indian regulators like RBI, SEBI, and IRDAI issue specific guidelines that act as mandatory control frameworks for entities under their purview. Your cybersecurity policy must incorporate these specific mandates.
By aligning your cybersecurity policy with one or more of these frameworks, you benefit from:
- Structured Approach: A systematic way to identify and implement necessary controls.
- Best Practices: Incorporating globally recognized security best practices.
- Compliance Support: Facilitating adherence to regulatory requirements and demonstrating due diligence.
- Benchmark: Providing a basis for measuring and improving your security posture.
The selected framework serves as a robust cyber security policy template for enterprises, guiding the development of specific policy clauses and ensuring that all critical security domains are addressed in your information security policy.
Core Policy Domains Every Enterprise Must Cover
A truly robust cybersecurity policy must be comprehensive, covering all critical aspects of an organization’s digital operations. These core policy domains form the bedrock of an effective information security framework.
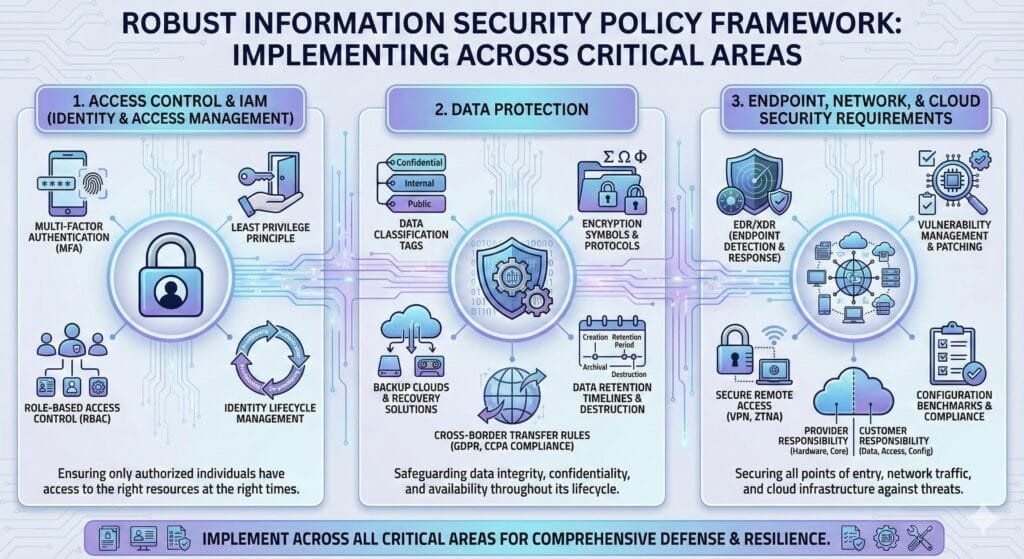
Access Control & Identity and Access Management (IAM)
Controlling who has access to what, and under what conditions, is fundamental. This domain of your cybersecurity policy should address:
- Least Privilege Principle: Users and systems should only be granted the minimum level of access necessary to perform their legitimate functions. This minimizes the impact of compromised accounts.
- Role-Based Access Control (RBAC): Define roles (e.g., ‘Finance Analyst’, ‘IT Administrator’) and assign permissions based on these roles, rather than individual users. This simplifies management and enhances consistency.
- Multi-Factor Authentication (MFA): Mandate MFA for all critical systems, remote access, and privileged accounts. This adds an essential layer of security beyond passwords.
- Privileged Access Management (PAM): Implement solutions and policies to secure, monitor, and manage privileged accounts (e.g., system administrators, database administrators). This includes just-in-time access, session recording, and password rotation.
- Identity Lifecycle Management: Establish clear procedures for user onboarding (account provisioning), role changes (access modification), and offboarding (account deactivation/deletion) to ensure access rights are always current and appropriate.
Data Protection
Data is the lifeblood of most organizations, and its protection is paramount, especially under regulations like India’s DPDPA 2023. This section of your information security policy should cover:
- Data Classification: Define categories for data based on its sensitivity and criticality (e.g., Public, Internal, Confidential, Restricted). This classification drives subsequent security controls.
- Encryption: Mandate encryption for sensitive data at rest (e.g., databases, file shares, cloud storage) and in transit (e.g., HTTPS, VPNs) to protect against unauthorized access.
- Data Retention and Disposal: Establish clear policies for how long different types of data must be retained (to meet legal/business requirements) and secure methods for its disposal when no longer needed.
- Backup and Recovery: Detail requirements for regular, verifiable backups of critical data, including offsite or immutable copies, and tested recovery procedures to ensure business continuity after a data loss event.
- Cross-Border Transfer Rules: Specify rules for transferring personal or sensitive data across national borders, ensuring compliance with local laws (like DPDPA 2023) and contractual agreements.
Endpoint, Network, and Cloud Security Requirements
The modern enterprise infrastructure spans endpoints, networks, and increasingly, complex cloud environments. Your cybersecurity policy must provide specific requirements for securing each of these critical layers.
Endpoint and Network Security
- Hardening Standards: Mandate secure configuration baselines for all endpoints (laptops, desktops, mobile devices) and network devices (routers, firewalls, switches). This includes disabling unnecessary services, strong password policies, and secure protocols.
- EDR/XDR Solutions: Require the deployment and continuous monitoring of Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions on all managed endpoints to detect and respond to advanced threats.
- Vulnerability Management and Patch SLAs: Establish a rigorous vulnerability management program, including regular scanning and penetration testing. Define Service Level Agreements (SLAs) for patching critical vulnerabilities within specified timeframes (e.g., 24-48 hours for critical, 7 days for high).
- Segmentation: Implement network segmentation (e.g., VLANs, micro-segmentation) to isolate critical systems and data, limiting the lateral movement of attackers in case of a breach.
- Secure Remote Access: Define clear policies for Virtual Private Network (VPN) usage, multi-factor authentication for remote access, and secure configuration requirements for devices used for remote work (e.g., mandatory endpoint security software).
- BYOD Guidance: If a Bring Your Own Device (BYOD) policy is in place, clearly outline security requirements for personal devices accessing corporate resources, including device enrollment, security software, and data segregation.
Cloud and SaaS Security
Cloud environments introduce new security paradigms, notably the shared responsibility model. Your information security policy must clearly address:
- Shared Responsibility Model: Explicitly define the split of security responsibilities between your organization and the Cloud Service Provider (CSP) for IaaS, PaaS, and SaaS environments. This is crucial for understanding your obligations.
- Minimum Security Baselines: Establish and enforce secure configuration baselines for all cloud resources (e.g., compute instances, storage buckets, network configurations) across all CSPs used. Use tools for continuous cloud security posture management (CSPM).
- Configuration Benchmarks: Mandate adherence to industry-recognized benchmarks (e.g., CIS Benchmarks for AWS, Azure, GCP) for cloud service configurations.
- Logging and Monitoring: Require comprehensive logging and monitoring of all cloud activities, including access logs, configuration changes, and API calls, integrated with your Security Information and Event Management (SIEM) system.
- Vendor Due Diligence: Prior to adopting any new cloud or SaaS service, mandate a thorough security due diligence process, assessing the vendor’s security controls, certifications, and contractual obligations.
These domain-specific policies are crucial steps to implement information security policy across your diverse technology landscape.
Third-Party, Supply Chain, and Outsourcing Policy
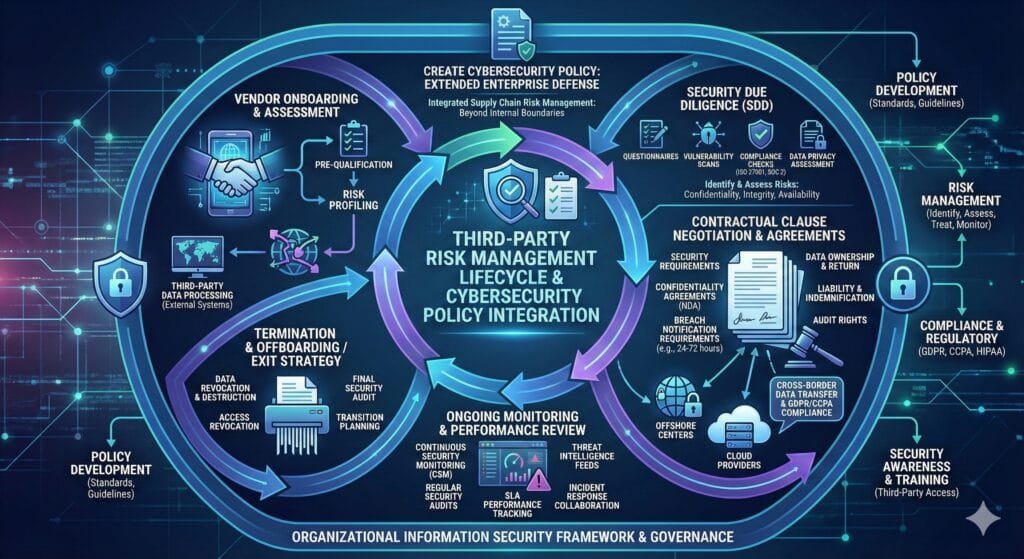
In 2025, an organization’s cybersecurity posture is only as strong as its weakest link, and often, that link resides within the supply chain or third-party ecosystem. A robust cybersecurity policy must extend beyond internal boundaries to address the risks posed by vendors, partners, and outsourced services. This is a critical component of your cyber risk management checklist.
Define Onboarding, Security Due Diligence, Contractual Clauses, and Ongoing Monitoring
Your information security policy must outline a systematic approach to managing third-party risks throughout their lifecycle:
Onboarding Process:
- Vendor Tiers: Classify vendors based on the criticality of their services and the level of access they require to your data or systems (e.g., critical, high, medium, low risk). This classification dictates the rigor of subsequent security assessments.
- Initial Risk Assessment: Before engagement, conduct a preliminary assessment to identify inherent risks associated with the vendor’s services.
Security Due Diligence:
- Questionnaires & Assessments: For higher-risk vendors, mandate comprehensive security questionnaires (e.g., SIG, CAIQ) and request evidence of their security controls (e.g., ISO 27001 certification, SOC 2 reports).
- On-site Audits: For critical vendors, reserve the right to perform on-site security audits or engage third-party auditors.
- Penetration Testing Review: Request proof of recent penetration tests and vulnerability assessments performed on their systems that interact with your organization.
Contractual Clauses:
- Mandatory Security Clauses: The cybersecurity policy must specify mandatory security clauses to be included in all vendor contracts. These should cover:
- Data protection requirements (aligned with DPDPA 2023).
- Breach notification obligations (including timelines and communication protocols).
- Right to audit clauses.
- Requirements for secure data disposal.
- Adherence to specific security standards (e.g., encryption, access control).
- Indemnification for security incidents caused by vendor negligence.
Ongoing Monitoring:
- Performance Reviews: Establish a process for periodically reviewing vendor security performance and compliance with contractual obligations.
- Threat Intelligence Integration: Integrate vendor risk monitoring with your threat intelligence feeds to be alerted to potential vulnerabilities or breaches affecting your critical third parties.
- Re-assessment: Mandate periodic re-assessment of vendor security posture, especially for critical vendors or after significant changes in their services or your data processing activities.
Address Data Processing by Third Parties, Offshore Centers, and Cloud Providers
Special attention must be paid to how third parties handle your data, particularly when it involves personal or sensitive information, offshore processing, or cloud environments.
- Confidentiality Agreements: Ensure robust Non-Disclosure Agreements (NDAs) and Data Processing Agreements (DPAs) are in place, explicitly detailing the vendor’s responsibilities for protecting your data.
- Breach Notification: The cybersecurity policy must stipulate clear, time-bound breach notification requirements for third parties, mirroring or exceeding your own internal and regulatory obligations (e.g., CERT-In, DPDPA 2023).
- Audit Rights: Reserve the right to audit the third party’s systems and processes relevant to your data, or require them to provide independent audit reports.
- Sub-processor Management: Require third parties to disclose their own sub-processors and ensure that similar security and contractual obligations flow down the supply chain.
- Offshore Processing: If data is processed in offshore centers, the policy must address specific legal and regulatory requirements for cross-border data transfer, ensuring adequate data protection safeguards are in place in the recipient country.
Integrating these elements into your information security policy is crucial for managing external risks and solidifying your overall information security framework.
Incident Response, Business Continuity, and Ransomware Playbooks
No matter how robust your preventive controls, cyber incidents are an inevitability. A well-defined Incident Response (IR) policy, integrated with Business Continuity Planning (BCP), Disaster Recovery (DR), and specialized ransomware playbooks, is critical for minimizing damage and ensuring organizational resilience. This is a cornerstone of your cyber risk management checklist.
Outline Mandatory Elements of an Incident Response Policy
Your cybersecurity policy must include a detailed IR plan that outlines the structured approach to managing security incidents:
- Roles and Responsibilities: Clearly define the Incident Response Team (IRT) members, their specific roles (e.g., Incident Commander, Technical Lead, Communications Lead, Legal Counsel), and responsibilities during an incident.
- Severity Levels: Establish a clear system for classifying incidents based on their impact and urgency (e.g., Critical, High, Medium, Low). This dictates response priorities and resource allocation.
- Escalation Paths: Define clear escalation matrices for different incident types and severity levels, ensuring that appropriate management and legal stakeholders are informed within defined timeframes.
- SLAs (Service Level Agreements): Set specific SLAs for incident detection, containment, eradication, recovery, and post-incident review. For example, “critical incidents must be contained within 2 hours.”
- Communications Plan: Develop a comprehensive communication strategy for internal stakeholders (employees, management), external parties (customers, media, partners), and regulatory bodies. This includes pre-approved templates and designated spokespersons.
- Post-Incident Reviews (Lessons Learned): Mandate a formal review process after every significant incident to analyze what went well, what could be improved, and to update policies, procedures, and controls accordingly.
Connect the Policy to Runbooks for Ransomware, Data Breach, and Major Outages
The overarching IR policy provides the framework, but specific runbooks (detailed step-by-step guides) are essential for effective execution during critical events.
Ransomware Playbooks:
- Containment: Immediate steps to isolate affected systems and prevent further spread.
- Eradication: Procedures for identifying the ransomware strain, removing it, and securing affected systems.
- Recovery: Detailed steps for restoring data from backups, rebuilding systems, and bringing services back online.
- Negotiation (if applicable): Guidelines for engaging with threat actors, including legal and ethical considerations (often discouraged by law enforcement).
- Decryption (if keys obtained): Procedures for using decryption tools.
- Communication: Specific templates for communicating with affected parties and regulators about a ransomware event.
Data Breach Playbooks:
- Identification: Procedures for confirming a data breach and identifying the scope of compromised data.
- Notification: Detailed steps for notifying affected individuals and relevant regulatory authorities (e.g., CERT-In, DPDPA 2023) within mandated timelines.
- Forensic Investigation: Guidelines for preserving evidence and conducting a forensic analysis to determine the root cause.
- Mitigation: Steps to prevent future similar breaches.
Major Outages (Integrating with BCP/DR):
- The IR policy should seamlessly integrate with the organization’s Business Continuity Plan (BCP) and Disaster Recovery (DR) plans.
- Failover Procedures: How to activate secondary systems and data centers.
- Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO): Defined targets for how quickly systems must be restored and how much data loss is acceptable.
- Dependency Mapping: Understanding critical interdependencies between systems and applications.
- Vendor Communication: Protocols for engaging with critical vendors during a major outage.
Regulator/Authority Reporting Expectations:
- Your cybersecurity policy must explicitly reference and incorporate the reporting requirements of bodies like CERT-In (e.g., 6-hour reporting for certain incidents) and the DPDPA 2023 (for personal data breaches).
- Outline the designated personnel responsible for these notifications and the information required.
Regular testing and simulation exercises (tabletop exercises, full-scale drills) of these playbooks are essential to ensure their effectiveness and train the IR team. This proactive approach to incident management is crucial for a comprehensive information security framework and effective cyber security governance.
Security Awareness, Culture, and Change Management
Technology and processes are only half the battle; people are often the weakest link in the security chain. A robust cybersecurity policy is ineffective if employees are unaware of its requirements or lack the necessary skills to adhere to them. Cultivating a strong security culture and managing change effectively are paramount for the success of your information security framework.
Specify Mandatory Trainings, Phishing Simulations, Secure Coding Awareness, and Tailored Programs
Your information security policy should explicitly mandate a comprehensive and ongoing security awareness program:
- Mandatory Annual Training: All employees, contractors, and relevant third parties must complete annual cybersecurity awareness training. This training should cover fundamental topics like password hygiene, identifying phishing attempts, safe browsing, data handling best practices, and the importance of reporting suspicious activity.
- Phishing Simulations: Conduct regular, unannounced phishing simulations to test employee vigilance and provide immediate, targeted training to those who fall for the lures. Track results to measure improvement and identify areas needing further education.
- Secure Coding Awareness: For development teams, implement specific training on secure coding practices, common vulnerabilities (e.g., OWASP Top 10), and integrating security into the Software Development Life Cycle (SDLC).
- Tailored Programs for Leadership and High-Risk Roles:
- Leadership: Executives and senior management require training focused on their specific responsibilities, such as understanding cyber risk at a strategic level, approving policy, and their role in incident response.
- High-Risk Roles: Employees with privileged access, those handling sensitive data, or those in finance/HR roles should receive specialized, more in-depth training relevant to their elevated risk profile.
- New Hire Onboarding: Integrate cybersecurity awareness as a mandatory component of new employee onboarding to instill security best practices from day one.
Define How Policy Changes Are Communicated, Tracked, and Enforced Across Distributed and Hybrid Workforces
Implementing a cybersecurity policy is not a one-time event. It’s an ongoing process that requires effective communication and reinforcement, especially in today’s distributed and hybrid work environments.
Communication Strategy:
- Multi-Channel Approach: Use various communication channels to disseminate policy updates (e.g., internal intranet, email announcements, team meetings, dedicated security portal).
- Clear and Concise Language: Translate technical policy jargon into easily understandable language, highlighting the “why” behind the policy and its benefits to the employee and the organization.
- Acknowledgement and Attestation: Require employees to formally acknowledge that they have read, understood, and agree to abide by the cybersecurity policy and any significant updates.
Tracking and Enforcement:
- Policy Management System: Utilize a system to track policy versions, approvals, and employee attestations.
- Performance Reviews: Integrate adherence to the cybersecurity policy into employee performance reviews where appropriate.
- Disciplinary Action: Clearly define the consequences of policy violations, ensuring fairness and consistency in enforcement. This should be communicated explicitly in the policy itself.
- Feedback Mechanisms: Establish channels for employees to ask questions about the policy or provide feedback, fostering a culture of open communication and continuous improvement.
By prioritizing security awareness and effective change management, organizations can transform their employees from potential vulnerabilities into a formidable first line of defense, strengthening the entire information security framework and achieving robust cyber security governance.
Metrics, Audits, and Continuous Improvement
A cybersecurity policy is not a static document; it’s a dynamic instrument that requires continuous monitoring, measurement, and refinement. This iterative approach is fundamental to maintaining an effective information security framework in the face of evolving threats and technologies. This section outlines how to measure policy effectiveness and drive continuous improvement within your cyber security governance.
Define KPIs/KRIs for Policy Effectiveness
To assess the effectiveness of your information security policy, you need to establish relevant Key Performance Indicators (KPIs) and Key Risk Indicators (KRIs). These metrics provide actionable insights for CIO/CISO dashboards and board reporting.
Key Performance Indicators (KPIs):
- Policy Exception Rate: The number or percentage of approved exceptions to the cybersecurity policy. A high rate might indicate policies are too restrictive or impractical.
- Incident Volume and Trends: The total number of security incidents over time, categorized by type (e.g., phishing, malware, unauthorized access). Helps identify common attack vectors.
- Mean Time To Detect (MTTD): The average time taken to identify a security incident from its occurrence. A lower MTTD indicates better detection capabilities.
- Mean Time To Respond (MTTR): The average time taken to contain and resolve an incident after detection. A lower MTTR indicates efficient incident response.
- Patch Compliance SLAs: The percentage of systems compliant with patching SLAs, indicating the effectiveness of vulnerability management.
- Security Awareness Training Completion Rate: Percentage of employees completing mandatory training.
- Phishing Failure Rates: Percentage of employees who clicked on simulated phishing links or submitted credentials. This measures user vigilance.
- Vulnerability Remediation Velocity: The speed at which identified vulnerabilities are fixed.
Key Risk Indicators (KRIs):
- Critical Vulnerability Exposure: The number of critical vulnerabilities present in production systems.
- Unapproved Access Attempts: Number of failed login attempts to critical systems.
- Privileged Account Activity: Anomalous activity detected on privileged accounts.
- Third-Party Security Rating: Aggregate security scores of critical vendors.
- Security Control Efficacy: Percentage of security controls functioning as intended.
These metrics enable data-driven decision-making, helping prioritize security investments and refine the cybersecurity policy.
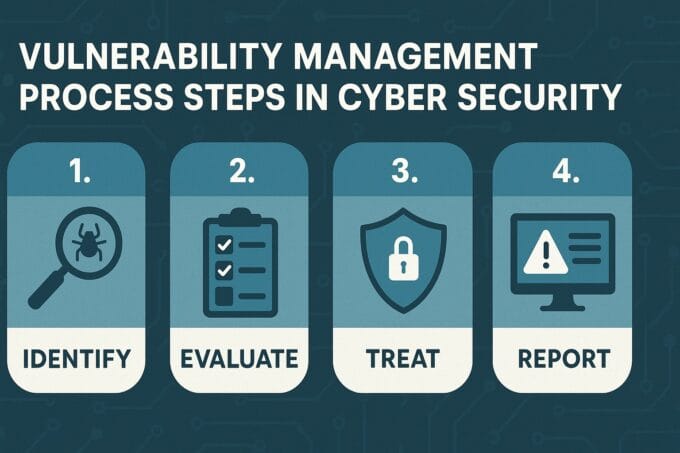
Explain Internal/External Audits, Testing Activities, and How Lessons Feed into Periodic Policy Reviews
Regular audits and testing are crucial verification mechanisms for the information security framework.
- Internal Audits: Conducted by an independent internal audit function, these assess compliance with the cybersecurity policy, identify control weaknesses, and recommend improvements.
- External Audits: Independent third-party auditors provide an objective assessment of your security posture against standards like ISO 27001, SOC 2, or regulatory requirements. These are often mandatory for compliance purposes.
Testing Activities:
- Penetration Testing (Pen Testing): Authorized simulated attacks against your systems to identify exploitable vulnerabilities before real attackers do.
- Red-Teaming: A more comprehensive exercise simulating a full-scope cyberattack, including social engineering and physical security components, to test the overall effectiveness of your defenses and incident response capabilities.
- Vulnerability Assessments: Regular automated and manual scans to identify security weaknesses in applications, networks, and systems.
- Security Control Testing: Periodic verification that specific security controls (e.g., MFA, encryption) are configured correctly and operating as intended.
Lessons Learned and Policy Reviews:
- Feedback Loop: Findings from audits, penetration tests, red-teaming exercises, and post-incident reviews must feed directly into the periodic review process of your cybersecurity policy.
- Adaptive Policy: This feedback ensures the policy remains current, addresses emerging threats, and incorporates lessons from real-world events.
- Board Reporting: Summaries of audit findings, testing results, and policy updates, along with the KPIs/KRIs, should be regularly presented to the Board and Risk Committee. This keeps senior leadership informed of the organization’s security posture and the continuous efforts in cyber risk management.
This cycle of definition, measurement, verification, and refinement is the essence of a living, adaptive, and truly robust information security framework, ensuring your cyber security governance remains effective in 2025 and beyond.
Practical Steps and Checklist for CIOs, CISOs, CTOs
Creating a robust cybersecurity policy is a significant undertaking, but breaking it down into manageable steps makes the process achievable. This checklist provides a pragmatic path for CIOs, CISOs, and CTOs to implement a comprehensive information security framework.
Concise Stepwise Checklist: How to Create a Cybersecurity Policy
Here’s a high-level roadmap for developing and implementing your organization’s cybersecurity policy:
- Assess Organizational Context:
- Map critical assets, data flows, and business processes.
- Identify all relevant Indian and sectoral regulatory obligations (DPDPA 2023, CERT-In, RBI/SEBI/IRDAI, etc.).
- Define the organization’s risk appetite.
- Perform a Comprehensive Risk Assessment:
- Identify threats, vulnerabilities, and potential business impacts.
- Prioritize risks (e.g., ransomware, data exfiltration, insider threats, cloud misconfigurations).
- Connect identified risks directly to necessary policy requirements.
- Define Governance and Roles (RACI):
- Establish board oversight, CISO mandate, and cross-functional security council.
- Assign clear ownership for policy creation, approval, review, and exception management.
- Select a Control Framework Baseline:
- Choose a primary framework (e.g., ISO 27001, NIST CSF) and integrate specific regulatory guidelines.
- This acts as your cyber security policy template for enterprises.
- Draft the Cybersecurity Policy Document:
- Cover core domains: Access Control & IAM, Data Protection, Endpoint/Network/Cloud Security, Third-Party Risk, Incident Response, and Security Awareness.
- Use clear, unambiguous language.
- Consult Stakeholders:
- Engage with IT, Legal, HR, Business Unit heads, and Privacy Officers to gather feedback and ensure practicality and buy-in.
- Address concerns and refine policy clauses based on input.
- Obtain Formal Approval:
- Secure approval from the Risk Committee and/or the Board of Directors, emphasizing the policy’s strategic importance.
- Communicate and Disseminate:
- Launch an internal campaign to introduce the new cybersecurity policy.
- Provide mandatory training for all employees, with attestation of understanding.
- Define a process for communicating future updates.
- Implement Controls and Enforce Policy:
- Roll out technical controls and operational procedures mandated by the policy.
- Integrate policy compliance into daily operations and disciplinary frameworks.
- Monitor, Audit, and Refine Continuously:
- Define and track KPIs/KRIs for policy effectiveness.
- Conduct regular internal and external audits, penetration tests, and red-teaming exercises.
- Use lessons learned from incidents and audits to periodically review and update the information security policy (at least annually).
Pragmatic Starting Path for Resource-Constrained Teams
For organizations with limited resources, attempting to implement a full-fledged information security framework all at once can be overwhelming. A pragmatic approach involves prioritizing where you focus your initial efforts:
- Focus on “Crown Jewels”: Identify your absolute most critical assets, data, and business processes (e.g., customer PII, intellectual property, core revenue-generating systems). Prioritize securing these first with the strongest controls from your cyber risk management checklist.
- Regulatory “Must-Haves”: Address non-negotiable compliance requirements immediately. In India, this means focusing on core mandates of DPDPA 2023 (data protection principles, breach notification) and CERT-In directions (incident reporting, log retention).
- High-Impact, Low-Cost Controls: Implement controls that offer significant security uplift for minimal investment. Examples include:
- Multi-Factor Authentication (MFA): Essential for all logins, especially privileged and remote access.
- Regular Backups (Offline & Immutable): Your last line of defense against ransomware.
- Basic Security Awareness Training: Educating employees on phishing and good password practices.
- Endpoint Protection: Reliable antivirus/anti-malware on all devices.
- Patch Management: Ensuring critical security updates are applied promptly.
- Strong Password Policy: Enforcing complexity and regular changes.
- Adopt a Phased Approach: Start with a foundational cybersecurity policy covering these critical areas, then progressively expand its scope and depth as resources become available. Use the chosen control framework (e.g., NIST CSF’s ‘Implement’ tier) as a guide for gradual maturity.
By following these practical steps and prioritizing wisely, any organization can begin the journey of how to create a cybersecurity policy that is robust, effective, and tailored to its unique environment, ensuring strong cyber security governance in the dynamic landscape of 2025.
Bottom Line
In 2025, the imperative for a robust cybersecurity policy is clearer than ever. It is not merely a technical document but a strategic business asset, vital for protecting your organization from the escalating threats of cyberattacks, navigating complex regulatory landscapes in India and globally, and sustaining digital transformation. From the foundational step of understanding your unique business and regulatory context to the continuous cycle of monitoring and improvement, every element of your information security framework contributes to your overall resilience.
By establishing clear cyber security governance, defining roles, leveraging recognized control frameworks, and meticulously crafting policies for every critical domain—from access control and data protection to third-party risk and incident response—you build a formidable defense. Crucially, fostering a strong security culture through continuous awareness and change management transforms your workforce into a proactive asset rather than a vulnerability.
The journey to an unassailable security posture is ongoing. Embrace the cyber risk management checklist outlined in this guide, commit to continuous improvement driven by metrics and audits, and ensure your cybersecurity policy remains adaptive and effective. Your organization’s future depends on it.
Actionable Next Steps:
- Initiate a Current State Assessment: Begin by mapping your critical assets and data flows and conducting a thorough regulatory compliance review specific to your operations in India.
- Form Your Security Council: Assemble a cross-functional team with representation from IT, Legal, HR, and key business units to collaborate on policy development and governance.
- Prioritize Your Top 3 Cyber Risks: Based on your initial risk assessment, identify the most pressing threats (e.g., ransomware, cloud misconfiguration) and start drafting policy clauses and controls to specifically mitigate these.
- Invest in Foundational Training: Launch mandatory cybersecurity awareness training for all employees and begin conducting regular phishing simulations.
- Schedule Your First Policy Review: Even a nascent policy needs a review schedule. Commit to reviewing and updating your cybersecurity policy at least annually, or more frequently if significant changes occur in your threat landscape or regulatory obligations.













Leave a comment