SCADA (Supervisory Control and Data Acquisition) systems control critical infrastructure, making them prime targets for cyberattacks. A breach can lead to catastrophic consequences, including power outages, water supply contamination, and industrial disasters. Strengthening SCADA cybersecurity is not just a technical necessity—it is a national security imperative. Before going to the cybersecurity aspects let’s understand its architecture first. Let’s understand how to Protect SCADA Systems.
SCADA Architecture Overview
A typical SCADA system architecture consists of several layers, each with distinct components and potential vulnerabilities.
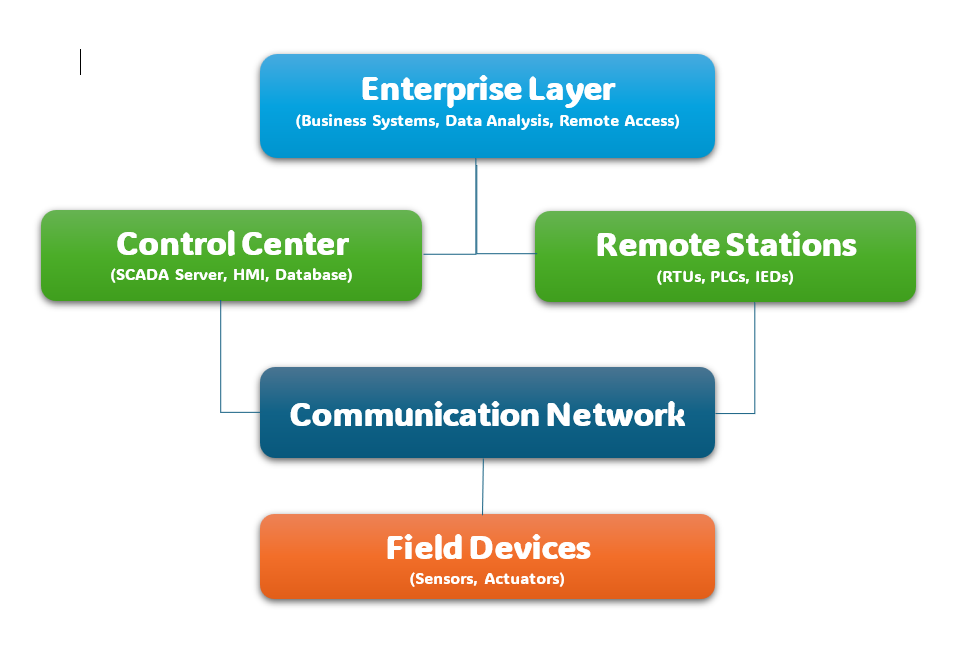
Common Cybersecurity Vulnerabilities in SCADA Systems
Many SCADA environments were designed decades ago, before cybersecurity was a primary concern. Common vulnerabilities include outdated software, weak authentication mechanisms, unpatched systems, and unsecured remote access. These weaknesses provide easy entry points for cyber adversaries seeking to exploit industrial control networks.
Layers and Their Vulnerabilities
Let’s break down each layer to understand where vulnerabilities may arise.
1. Field Devices Layer
Components:
- Sensors and Actuators: Measure physical parameters and execute control commands.
- Field Instruments: Interface directly with the physical processes.
Vulnerabilities:
- Physical Tampering: Devices are often in remote locations, making them susceptible to unauthorized access.
- Lack of Authentication: Many legacy devices do not support authentication mechanisms.
- Firmware Weaknesses: Outdated firmware may contain exploitable vulnerabilities.
Vulnerabilities and Mitigation Strategies
| Vulnerabilities | Impact | Mitigation Strategies |
|---|---|---|
| Physical Tampering | Unauthorized control or data manipulation | Implement physical security measures (locks, surveillance) |
| Lack of Authentication | Unauthorized access and control | Upgrade to devices supporting authentication |
| Firmware Weaknesses | Exploitation leading to malfunction | Regularly update firmware |
2. Communication Network Layer
Components:
- Wired/Wireless Networks: Connect field devices to control centers.
- Protocols: Commonly use Modbus, DNP3, or proprietary protocols.
Vulnerabilities:
- Unencrypted Data Transmission: Data sent in plain text can be intercepted (e.g., via man-in-the-middle attacks).
- Insecure Protocols: Legacy protocols lack encryption and authentication.
- Network Segmentation Issues: Flat networks allow attackers to move laterally once inside.
Vulnerabilities and Mitigation Strategies
| Vulnerabilities | Impact | Mitigation Strategies |
|---|---|---|
| Unencrypted Data Transmission | Data interception and manipulation | Implement encryption (TLS, VPN) |
| Insecure Protocols | Unauthorized access and data compromise | Use secure protocols or wrappers (e.g., Secure Modbus) |
| Network Segmentation Issues | Spread of malware across network | Implement VLANs, firewalls, and DMZs |
3. Control Center Layer
Components:
- SCADA Servers: Central processing units for data collection and control commands.
- Human-Machine Interfaces (HMIs): Allow operators to interact with the system.
- Databases: Store historical data and system configurations.
Vulnerabilities:
- Malware Attacks: Control centers can be targeted with viruses or ransomware.
- Unauthorized Access: Weak authentication can lead to unauthorized users gaining control.
- Software Vulnerabilities: Unpatched systems may have exploitable bugs.
Vulnerabilities and Mitigation Strategies
| Vulnerabilities | Impact | Mitigation Strategies |
|---|---|---|
| Malware Attacks | System shutdown, data loss | Use antivirus, apply patches, regular backups |
| Unauthorized Access | Control manipulation, data theft | Enforce strict access controls, multi-factor authentication |
| Software Vulnerabilities | System compromise | Regular updates and vulnerability scanning |
4. Enterprise Layer
Components:
- Business Systems: Analytics, reporting, and enterprise resource planning (ERP) systems.
- Remote Access Services: VPNs and remote desktops for maintenance and monitoring.
Vulnerabilities:
- Remote Access Exploits: Improperly secured remote access can be a gateway for attackers.
- Insider Threats: Employees with malicious intent or compromised credentials.
- Integration Risks: Connection between IT and OT (Operational Technology) networks increases exposure.
Vulnerabilities and Mitigation Strategies
| Vulnerabilities | Impact | Mitigation Strategies |
|---|---|---|
| Remote Access Exploits | Unauthorized network entry | Secure remote access with MFA, monitoring |
| Insider Threats | Data breaches, sabotage | Employee training, least privilege principles |
| Integration Risks | Cross-network contamination | Network segmentation, strict interface controls |
Visualizing Vulnerabilities
Potential Attack Paths
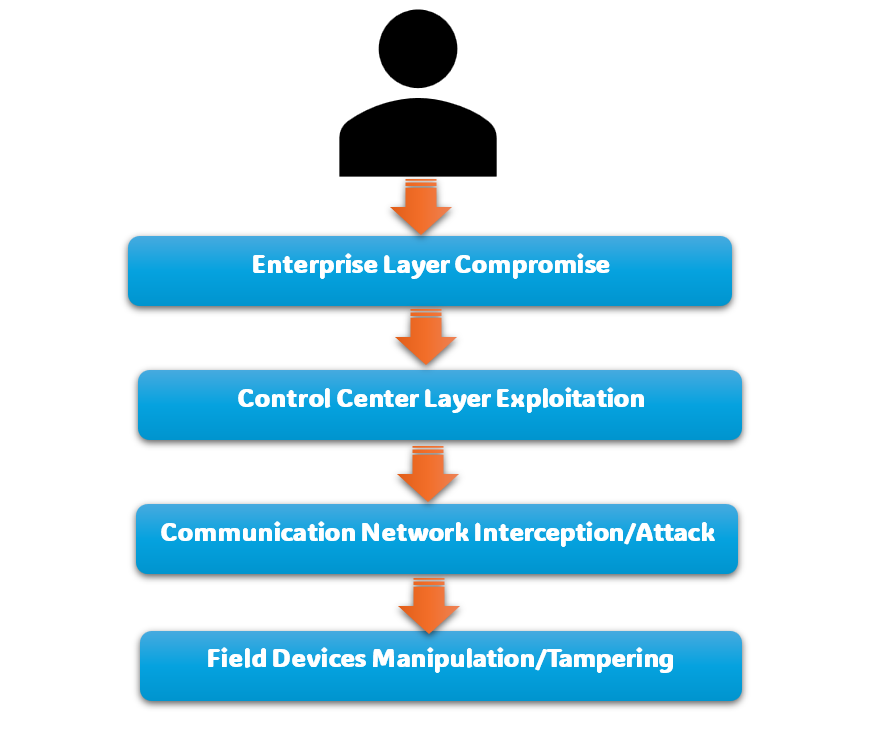
Understanding SCADA Cyber Threats
Early cyber threats targeting SCADA systems were simplistic, often exploiting weak passwords or misconfigurations. Today, adversaries deploy sophisticated tactics, including ransomware, advanced persistent threats (APTs), and zero-day exploits. Cyberwarfare tactics increasingly incorporate SCADA-specific attack vectors, making proactive defense strategies essential.
How Attackers Exploit SCADA System Weaknesses
Hackers use phishing campaigns, malware, and insider threats to gain unauthorized access to SCADA environments. Poorly segmented networks allow attackers to pivot from IT systems to operational technology (OT) networks, escalating their ability to cause disruptions.
Real-World Examples of SCADA System Breaches
Infamous attacks like Stuxnet, which targeted Iran’s nuclear program, and the 2015 Ukrainian power grid attack showcase the devastating potential of SCADA cyber threats. These incidents highlight the urgent need for robust cybersecurity frameworks.
Key Security Risks Facing SCADA Systems
Following are some of the key security issues reported by various industry users.
Unsecured Remote Access and Insider Threats
Remote access is essential for SCADA operations, but weak authentication and unsecured connections provide an easy entry point for attackers. Insider threats—whether malicious or accidental—also pose significant risks.
Outdated Software and Legacy System Vulnerabilities
Many SCADA systems still run on outdated operating systems, which no longer receive security updates. This makes them highly vulnerable to exploitation.
Malware, Ransomware, and Advanced Persistent Threats
Malware attacks targeting SCADA systems are increasing, with ransomware operators recognizing the high-stakes nature of industrial environments. APTs, often backed by nation-states, pose an even greater threat due to their long-term infiltration tactics.
Supply Chain Risks and Third-Party Vendor Exploits
Attackers frequently exploit vulnerabilities in third-party software and hardware components. Weak supply chain security can introduce backdoors into SCADA networks.
Best Practices for Securing SCADA Systems
Securing SCADA (Supervisory Control and Data Acquisition) systems is crucial to ensure the safety and reliability of critical infrastructure. Here are some best practices for securing SCADA systems:
Implementing a Robust Network Segmentation Strategy
Separating IT and OT networks minimizes attack surfaces. Proper segmentation ensures that an IT breach does not easily compromise critical industrial controls.
The Importance of Regular Software Updates and Patch Management
Timely updates prevent attackers from exploiting known vulnerabilities. Organizations must prioritize patching while ensuring uptime and operational stability.
Enhancing Authentication and Access Control Measures
Multi-factor authentication (MFA) and role-based access controls (RBAC) help restrict unauthorized access to SCADA systems.
Using Encryption to Protect Data in Transit and at Rest
Strong encryption ensures that sensitive SCADA data remains secure, even if intercepted by attackers.
Developing a Comprehensive Incident Response Plan
A well-defined incident response strategy enables rapid containment and mitigation of cyber threats.
Advanced Cybersecurity Technologies for SCADA Protection
How AI and Machine Learning Can Detect Anomalies
Artificial intelligence (AI) enhances threat detection by identifying unusual patterns in SCADA network traffic.
The Role of Intrusion Detection and Prevention Systems (IDPS)
IDPS solutions monitor network activity, blocking suspicious behavior before it can escalate into a full-scale attack.
Security Information and Event Management (SIEM) for Real-Time Monitoring
SIEM platforms centralize log data and provide real-time analytics, helping security teams respond swiftly to threats.
The Future of Zero-Trust Architecture in SCADA Security
Zero-trust security models eliminate implicit trust, requiring continuous authentication and strict access controls.
Regulatory and Compliance Considerations
Understanding NERC CIP, IEC 62443, and Other Industry Standards
Regulatory frameworks like NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) and IEC 62443 provide guidelines for securing SCADA systems.
How Compliance Frameworks Improve SCADA Security Posture
Adhering to compliance standards strengthens security, reduces legal liabilities, and builds stakeholder confidence.
The Role of Government Regulations in Securing Critical Infrastructure
Governments worldwide are implementing stricter regulations to protect industrial control systems from cyber threats.
Training and Awareness for SCADA Security
Educating Employees on Cyber Hygiene and Social Engineering Risks
Employees must be trained to recognize phishing attacks, avoid risky behaviors, and follow cybersecurity best practices.
Conducting Regular Security Audits and Penetration Testing
Frequent security assessments help identify vulnerabilities before attackers can exploit them.
The Need for Continuous Monitoring and Threat Intelligence Sharing
Proactive threat intelligence sharing across industries strengthens collective SCADA security defenses.
Final Thoughts
The Future of SCADA Security in an Increasingly Connected World
As industrial systems become more interconnected, SCADA security must evolve to counter emerging cyber threats.
Actionable Steps to Strengthen SCADA Cybersecurity Today
Organizations must implement best practices, invest in advanced cybersecurity tools, and prioritize employee training.
Why a Proactive Security Approach Is Essential for SCADA Protection
Waiting for an attack is not an option. A proactive, multi-layered defense strategy is crucial for safeguarding SCADA systems and critical infrastructure. Hope you must have some understanding and best practices about how to Protect SCADA Systems.
















Leave a comment