Kumar S
Kumar is a cybersecurity professional with over 20 plus years of experience in the industry, currently serving as Chief Information Security Officer (CISO) at a prominent organization. In addition to his executive role, he holds the position of Editor-in-Chief at Cyber Tech Journals, where he contributes to advancing cybersecurity knowledge and best practices.
A Practical Guide to Phishing Awareness for Employees
In today’s digital-first business landscape, phishing is more than just a nuisance—it’s a serious threat to your finances, your reputation, and your data....
ByKumar SJune 30, 2025Cloud Security Best Practice for Enterprises: A CISO’s Guide
In today’s fast-paced digital world, businesses are moving to the cloud faster than ever before. This move brings amazing benefits like more flexibility,...
ByKumar SJune 20, 2025Beyond the Hacker: Exploring Diverse Career Paths in Cyber Security
Cybersecurity is far more than ethical hacking. As the industry expands, organizations need specialists in governance, incident response, cloud security, intelligence, and leadership....
ByKumar SJune 19, 2025Cybersecurity for Healthcare Providers: Protecting Patient Data in a Digital Age
The healthcare industry has embraced digital transformation at breakneck speed—electronic health records (EHRs), telemedicine, AI diagnostics, and connected medical devices are now integral....
ByKumar SJune 9, 2025ISO 27001 Certification: Process, Audit, Checklist & SOC 2 Comparison
In a world plagued by cyber threats, protecting information assets is no longer optional. For organisations serious about information security, ISO 27001 certification...
ByKumar SJune 9, 2025Fake Job Offers Scam: How to Spot & Avoid Recruitment Frauds
In today’s dynamic job market, the pursuit of new career opportunities often begins online. While the digital landscape has revolutionized how we connect...
ByKumar SJune 5, 2025QR Code Scams (Quishing): The New-Age Digital Trap
QR code scams—also known as quishing—are the latest weapon in a cybercriminal’s arsenal. From fake parking payments to restaurant menus and UPI fraud,...
ByKumar SJune 4, 2025WhatsApp & SMS Scams: How They Work and How to Stay Protected
Have you ever received a text message or a WhatsApp chat from an unknown number, asking for personal details, promising a prize, or...
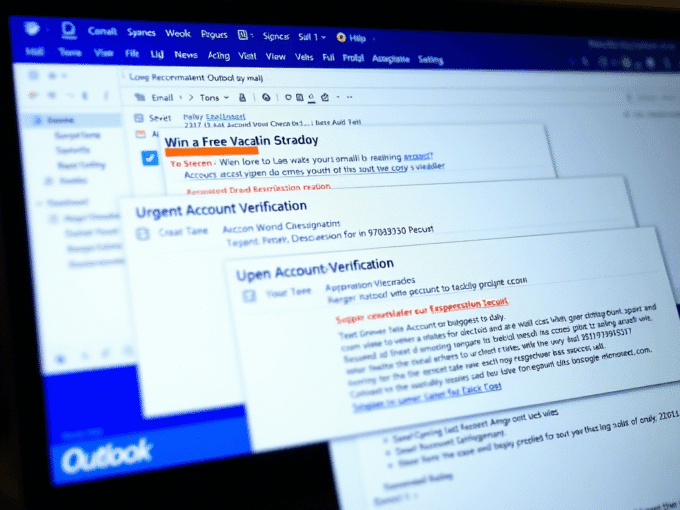
ByKumar SJune 4, 2025Phishing & Email Scams: How to Spot Them and Stay Safe
You check your email and see a message from your bank. It looks urgent — something about suspicious activity on your account. You...
ByKumar SJune 4, 2025