In today’s fast-paced digital world, businesses face a constant barrage of cyber threats. Among these, phishing attacks stand out as one of the most common and damaging. These tricky attacks often fool employees into giving up sensitive information or clicking on harmful links, leading to massive data breaches, financial losses, and damage to a company’s reputation. Even the most advanced technical defenses can be bypassed if just one employee falls victim to a clever phishing email.
For enterprise-level organizations, the stakes are incredibly high. A single successful phishing attempt can trigger a chain reaction, compromising critical systems, exposing customer data, and disrupting operations. This isn’t just a technical problem; it’s a business risk that demands a comprehensive, multi-layered approach. It’s no longer enough to rely on a single solution; instead, organizations must build a strong “human firewall” alongside robust technological and process-based defenses.
This article will dive deep into how enterprises can strengthen phishing defence mechanisms. We’ll explore practical, layered protection strategies that combine cutting-edge technology, effective employee training, and well-defined operational processes to create a resilient defense against this ever-evolving threat.
Key Takeaways
- Phishing is an Evolving Threat: Phishing attacks are becoming more sophisticated, targeting human vulnerabilities and bypassing traditional defenses, making a layered approach essential.
- Three Pillars of Defense: Effective phishing defense relies on a strong combination of Technology (like email gateways and MFA), People (through continuous security awareness training), and Process (robust incident response plans).
- The Human Element is Key: Employees are both the primary target and the strongest defense. Regular, engaging training and a positive security culture are crucial to empower them as “human firewalls.”
- Continuous Improvement is Non-Negotiable: Phishing tactics constantly change. Organizations must regularly assess their defenses, update strategies, and adapt to new threats to maintain effectiveness.
- Proactive Measures Save Millions: Investing in layered phishing defense and incident response planning is far more cost-effective than dealing with the aftermath of a successful breach.
Understanding the Phishing Threat Landscape: Why It’s So Dangerous
Phishing is a type of cybercrime where attackers pretend to be a trustworthy entity (like a bank, a well-known company, or even a colleague) to trick individuals into revealing sensitive information, such as usernames, passwords, credit card details, or other personal data. They often do this through email, text messages (smishing), or phone calls (vishing).
The Many Faces of Phishing
While the goal is always similar, phishing attacks come in many forms, each with its own twist:
- Spear Phishing: Highly targeted attacks aimed at specific individuals, often using personal information to make the scam more believable. Imagine an email pretending to be from your HR department asking you to “update your benefits.”
- Whaling: A type of spear phishing that targets high-profile individuals within an organization, like CEOs or CFOs. The goal is often to trick them into approving fraudulent wire transfers or revealing highly confidential information.
- Business Email Compromise (BEC): A sophisticated scam where attackers gain access to a corporate email account or spoof an executive’s email to trick employees (often in finance) into transferring money or sensitive data to the attackers. The FBI reported BEC scams cost businesses over $2.7 billion in 2022 alone!
- Smishing (SMS Phishing): Phishing attempts delivered via text messages. These often contain links to malicious websites or prompt you to call a fake customer service number.
- Vishing (Voice Phishing): Phishing attempts conducted over the phone. Attackers might impersonate technical support, law enforcement, or bank officials to trick victims into revealing information or performing actions.
- Pharming: Redirecting users from legitimate websites to fake ones without their knowledge, even if they type the correct web address. This is often done by poisoning DNS records.
Here’s a quick look at the different types:
| Phishing Type | Description | Common Target | Example Scenario |
|---|---|---|---|
| Standard Phishing | Broad, untargeted emails designed to trick many people. | General Public | A fake “password reset” email from a popular online service. |
| Spear Phishing | Highly targeted, personalized attacks. | Specific Individuals | An email appearing to be from your manager, asking you to review a “confidential document.” |
| Whaling | Targets senior executives or high-value individuals. | CEOs, CFOs, Executives | An email impersonating a CEO, instructing the finance department to make an urgent wire transfer. |
| BEC (Business Email Compromise) | Attackers compromise or spoof business email accounts to facilitate fraudulent transfers or data exfiltration. | Employees with Financial Access | An email from a “vendor” with updated bank details for an invoice, or an email from a “CEO” requesting W-2 forms for “urgent review.” |
| Smishing | Phishing via SMS (text messages). | Mobile Users | A text message from a “bank” warning of suspicious activity and asking you to click a link to verify your account. |
| Vishing | Phishing via voice calls. | Phone Users | A call from someone claiming to be tech support, saying your computer has a virus and asking for remote access or personal information. |
| Pharming | Redirects users to fake websites, even if they type the correct URL, often by manipulating DNS. | Anyone on the internet | Typing www.yourbank.com but being redirected to a malicious site that looks identical, due to a compromised DNS server. |
Why Phishing Works: The Human Element
Despite advancements in security technology, phishing remains incredibly effective because it preys on human nature. Attackers use social engineering tactics, playing on emotions like fear, urgency, curiosity, or greed.
- Urgency: “Your account will be suspended if you don’t click this link now!”
- Fear: “Suspicious activity detected on your account – click here to secure it!”
- Curiosity: “Check out these embarrassing photos of you!”
- Authority: “This is your CEO, I need you to transfer funds immediately.”
These tactics often lead people to act quickly without thinking critically, bypassing the technical defenses that might otherwise catch the malicious content.
Cybercriminals are like water; they will always find the path of least resistance. Often, that path leads directly through the human element. No technology, however sophisticated, can completely negate the power of social engineering.
The Imperative for Layered Phishing Defense: Building a Stronger Wall
Imagine a castle with only one wall. If an enemy breaches that wall, the castle falls. Now imagine a castle with multiple walls, moats, drawbridges, and guards positioned at every turn. Even if an enemy gets past the first line of defense, they face many more obstacles.
This is the concept behind a “layered defense” or “defense in depth” strategy. For phishing, it means not relying on a single security solution but implementing multiple, overlapping controls that work together. If one layer fails, another is there to catch the threat. This approach significantly increases the effort and resources an attacker needs to succeed, often making them give up and move on to easier targets.
Think of it like the “Swiss Cheese Model” of accident causation. Each slice of Swiss cheese has holes (vulnerabilities). If you stack many slices, it’s unlikely that all the holes will line up perfectly, preventing a direct path through. Similarly, multiple security layers reduce the chance of a successful attack.
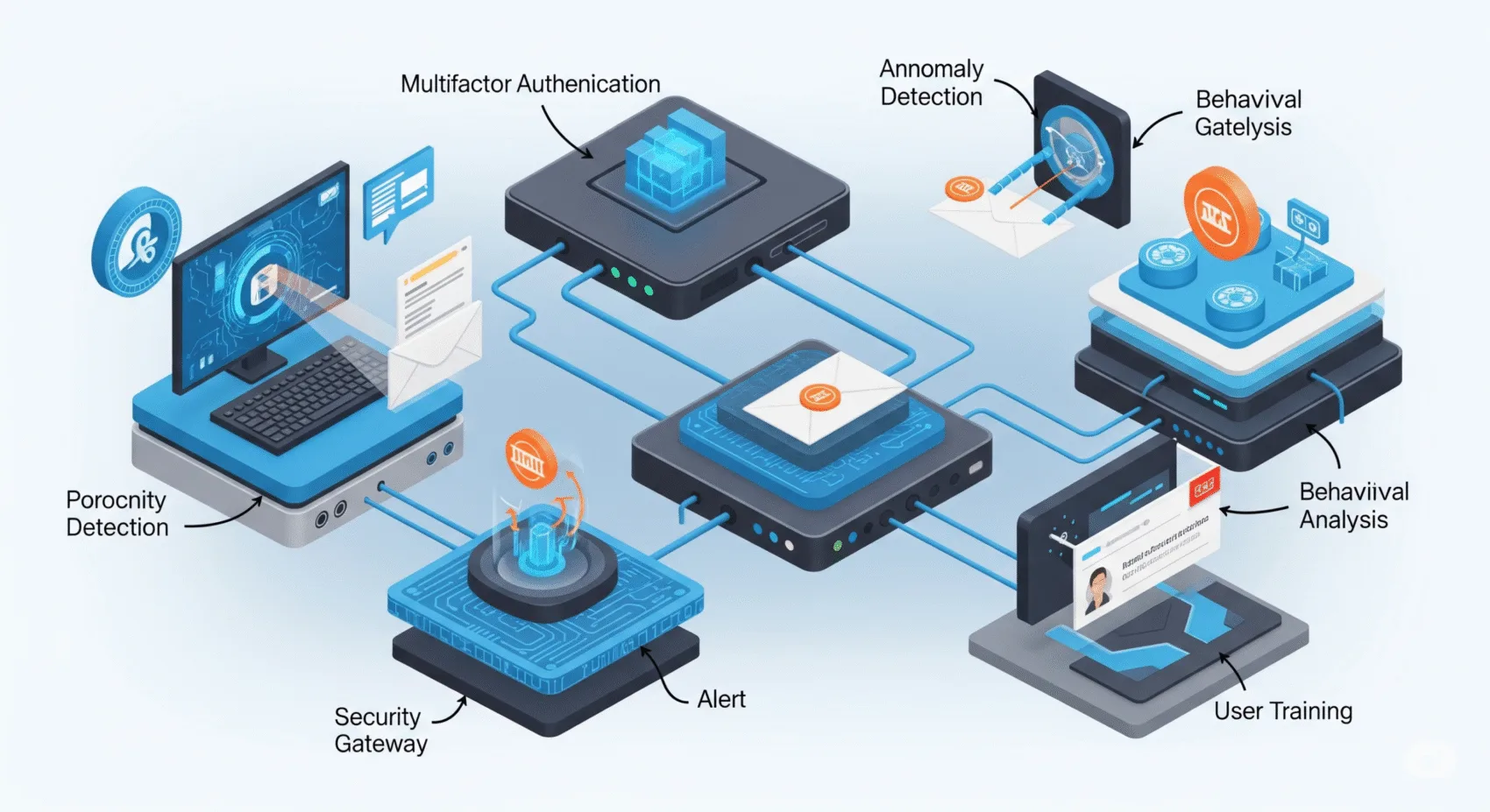
Layer 1: Technology – Fortifying the Digital Gates
Technology forms the foundational layer of any robust phishing defense. These tools are designed to detect, block, and mitigate phishing attempts before they even reach an employee’s inbox or device.
1. Advanced Email Gateway Security
Your email gateway is the first line of defense. Modern gateways do more than just block spam; they use sophisticated techniques to identify and quarantine phishing emails.
- Spam and Phishing Filters: Use artificial intelligence (AI) and machine learning (ML) to analyze email headers, content, links, and attachments for suspicious patterns.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC), Sender Policy Framework (SPF), and DomainKeys Identified Mail (DKIM): These email authentication protocols help verify that incoming emails are legitimate and prevent attackers from spoofing your domain. Implementing them correctly is vital.
- SPF: Lists authorized servers that can send email for your domain.
- DKIM: Adds a digital signature to outgoing emails, verifying the sender and ensuring the message hasn’t been tampered with.
- DMARC: Tells receiving email servers what to do if an email fails SPF or DKIM checks (e.g., quarantine, reject, or allow but report).
- URL Rewriting and Sandboxing: Links in emails are often rewritten to point to a safe proxy that scans the linked page for malicious content in real-time. Attachments can be “sandboxed” – opened in a secure, isolated environment to see if they perform malicious actions before reaching the user.
2. Endpoint Detection and Response (EDR)
Even if a phishing email slips through, EDR solutions on employee devices (endpoints) can detect and respond to malicious activity.
- Behavioral Analysis: EDR monitors system processes, network connections, and file access for unusual behavior that might indicate a compromise (e.g., a legitimate program trying to access sensitive files or connect to a suspicious IP address).
- Automated Response: Can automatically isolate a compromised device, terminate malicious processes, or roll back changes.
3. Multi-Factor Authentication (MFA) 🔐
MFA is one of the most effective technical controls against credential-phishing attacks. Even if an attacker steals a user’s password, they still need a second form of verification (like a code from a mobile app, a fingerprint, or a hardware token) to gain access.
- Implement MFA Everywhere: Apply MFA to all critical systems, applications, and VPNs, especially those accessible from outside the corporate network.
- Strong MFA Methods: Prioritize phishing-resistant MFA methods like FIDO2/WebAuthn hardware tokens over SMS-based codes, which can be intercepted.
4. Web Content Filtering and DNS Filtering
These tools block access to known malicious websites, including those used in phishing campaigns.
- Web Content Filtering: Prevents users from accessing categories of websites deemed inappropriate or risky (e.g., gambling, adult content, or known malware sites).
- DNS Filtering: Blocks DNS requests to malicious domains, preventing users from connecting to phishing sites even if they click a bad link. This is a crucial “early warning” system.
5. Security Information and Event Management (SIEM) / Security Orchestration, Automation, and Response (SOAR)
These advanced platforms collect and analyze security logs from across your entire IT environment, helping security teams quickly detect and respond to threats.
- SIEM: Aggregates logs, correlates events, and generates alerts based on suspicious activity, helping identify potential phishing campaigns or post-phishing compromises.
- SOAR: Automates security operations, allowing for faster response to incidents. For example, if a phishing email is detected, SOAR can automatically block the sender, scan affected mailboxes, and alert the security team.
Here’s a summary of key technologies:
| Technology Layer | Primary Function | Benefit Against Phishing |
|---|---|---|
| Email Gateway Security | Filters, scans, and authenticates incoming/outgoing emails. | Blocks malicious emails before they reach user inboxes; prevents domain spoofing. |
| Endpoint Detection & Response (EDR) | Monitors device activity for threats, provides incident response capabilities. | Detects and contains malware/ransomware if a user clicks a malicious link or opens an infected attachment. |
| Multi-Factor Authentication (MFA) | Requires multiple forms of verification for user access. | Prevents unauthorized access even if passwords are stolen via phishing. |
| Web & DNS Filtering | Blocks access to malicious websites and domains. | Prevents users from reaching phishing sites or downloading malware from compromised links. |
| SIEM/SOAR | Collects security data, analyzes threats, and automates responses. | Provides early detection of phishing campaigns, speeds up incident response, identifies compromised accounts. |
| Data Loss Prevention (DLP) | Monitors and prevents sensitive data from leaving the organization. | Prevents employees from inadvertently sending confidential data to phishing attackers or external unauthorized parties. |
Layer 2: People – Empowering the Human Firewall
While technology is crucial, the human element remains the most targeted and, potentially, the most vulnerable link. However, with the right training and culture, employees can become your strongest defense.
1. Comprehensive Security Awareness Training
Training shouldn’t be a one-time event or a boring annual slideshow. It needs to be continuous, engaging, and relevant.
- Regular, Interactive Training: Conduct frequent, short, and interactive training sessions covering the latest phishing tactics. Use real-world examples and make it relatable.
- Simulated Phishing Exercises: Regularly send simulated phishing emails to employees. This is a critical tool to test their awareness in a safe environment.
- Provide Immediate Feedback: If an employee clicks a simulated phishing link, they should immediately receive targeted training explaining what they missed and how to identify such threats in the future.
- Positive Reinforcement: Celebrate employees who report suspicious emails. Avoid shaming those who click, as this discourages reporting.
- Reporting Mechanisms: Make it easy for employees to report suspicious emails. Provide a clear, simple button or process (e.g., a “Report Phish” button in their email client). This not only helps identify attacks but also reinforces good behavior.
- Role-Based Training: Tailor training to different roles. Executives might need specific training on whaling and BEC attacks, while finance teams need to be vigilant about invoice fraud.
2. Cultivating a Security-Conscious Culture
Security awareness goes beyond just training; it’s about building a culture where security is everyone’s responsibility.
- Leadership Buy-in: When leaders actively champion security, it sends a powerful message. If the CEO participates in phishing simulations, others will follow suit.
- Open Communication: Encourage employees to ask questions and report concerns without fear of reprisal. Create a safe space for learning and improvement.
- Gamification and Incentives: Consider making security training fun. Offer small rewards or recognition for high reporting rates or low click rates in simulations.
- “See Something, Say Something”: Empower employees to be vigilant and report anything that looks “off.” This collective vigilance significantly strengthens your defense.
Your employees are your first line of defense, not your weakest link. Invest in them, empower them, and they will become your most formidable cybersecurity asset.
Layer 3: Process – Establishing Robust Operational Defenses
Even with the best technology and the most aware employees, some phishing attempts will inevitably succeed. That’s where strong processes come into play, minimizing damage and ensuring rapid recovery.
1. Incident Response Plan (IRP)
A well-defined and regularly practiced IRP is crucial for responding to successful phishing attacks. It should outline clear steps for:
- Detection: How are phishing incidents identified (e.g., employee reports, SIEM alerts)?
- Analysis: How is the scope of the attack determined (e.g., who clicked, what data was accessed)?
- Containment: How are affected systems or accounts isolated to prevent further spread?
- Eradication: How is the threat removed (e.g., malware removal, credential resets)?
- Recovery: How are systems restored to normal operation?
- Post-Incident Review: What lessons are learned to prevent future occurrences?
- Regular Drills: Conduct tabletop exercises and live simulations to test the IRP. This helps identify weaknesses and ensures that teams know their roles during a real incident.
- Communication Plan: Define who communicates what, when, and how, both internally and externally (e.g., customers, regulators, law enforcement).
2. Vulnerability Management and Patch Management
Phishing attacks often exploit known software vulnerabilities. Keeping systems updated is a critical preventative measure.
- Vulnerability Management: Regularly scan your networks and applications for vulnerabilities. Prioritize and remediate critical flaws.
- Patch Management: Ensure all operating systems, applications, and firmware are regularly updated with the latest security patches. Automate this process where possible.
3. Strict Access Control Policies
Limiting access to sensitive data and systems reduces the potential damage if an account is compromised via phishing.
- Principle of Least Privilege (PoLP): Users should only have the minimum access rights necessary to perform their job functions.
- Role-Based Access Control (RBAC): Assign permissions based on user roles rather than individual users.
- Regular Access Reviews: Periodically review user access rights to ensure they are still appropriate.
4. Data Backup and Recovery
In the event of a successful ransomware attack (often delivered via phishing), having robust backups is your last line of defense.
- Regular Backups: Implement a comprehensive backup strategy for all critical data and systems.
- Offline/Immutable Backups: Store backups offline or in immutable formats to protect them from ransomware encryption.
- Test Restorations: Regularly test your ability to restore data from backups to ensure they are viable.
5. Vendor Risk Management
Your supply chain can be a weak link. Phishing attacks sometimes originate from compromised vendor accounts.
- Assess Vendor Security: Evaluate the cybersecurity posture of third-party vendors who have access to your systems or data.
- Contractual Requirements: Include security clauses in vendor contracts, requiring them to meet certain security standards and promptly report breaches.
Advanced Phishing Threats and Future Trends: Staying Ahead of the Curve
The phishing landscape is constantly evolving. Attackers are leveraging new technologies and adapting their tactics.
- AI-Powered Phishing: Generative AI tools can create highly convincing phishing emails, complete with perfect grammar and contextually relevant content, making them much harder to spot. They can also generate realistic fake voices for vishing.
- QR Code Phishing (Quishing): Attackers embed malicious QR codes in emails, physical flyers, or even legitimate documents. Scanning the code leads to a phishing site.
- Deepfakes and Voice Cloning: The rise of deepfake technology could lead to highly sophisticated vishing or video-based phishing attacks where attackers impersonate executives with uncanny realism.
- Supply Chain Attacks: Phishing can be part of a larger supply chain attack, where a less secure vendor is compromised to gain access to a larger target.
- SMS and Messaging App Phishing: As more communication shifts to messaging apps, these platforms become new targets for phishing.
To combat these emerging threats, enterprises must embrace:
- Threat Intelligence: Stay informed about the latest phishing trends, tactics, and indicators of compromise (IOCs).
- Adaptive Security: Continuously adjust your security controls and training programs based on new threats.
- Zero Trust Architecture: Assume no user or device is inherently trustworthy, even inside the network. Verify everything.
Measuring and Improving Your Phishing Defense: The Path to Resilience
You can’t manage what you don’t measure. To truly strengthen phishing defence, enterprises must track their effectiveness and continuously seek improvement.
Key Performance Indicators (KPIs)
Monitor these metrics to gauge your phishing defense posture:
- Phishing Simulation Click-Through Rate (CTR): The percentage of employees who click on simulated phishing links. A lower CTR indicates better awareness. Target a low single-digit percentage.
- Imagine a graph here showing the decline in simulated phishing click rates over time, correlating with increased training frequency.
- Phishing Email Reporting Rate: The percentage of suspicious emails reported by employees. A higher rate indicates a more vigilant workforce.
- Time to Detect (TTD): How quickly your security team identifies a real phishing campaign or compromise.
- Time to Respond (TTR): How quickly your team contains and remediates a phishing incident.
- Number of Successful Phishing Breaches: The ultimate measure. Aim for zero.
- Cost of Phishing Incidents: Track financial losses, recovery costs, and reputational damage from successful attacks.
Regular Audits and Assessments
- Penetration Testing: Engage ethical hackers to simulate real-world phishing attacks and attempt to breach your defenses.
- Security Audits: Regularly review your security configurations, policies, and procedures to ensure they are aligned with best practices and compliance requirements (e.g., NIST Cybersecurity Framework, ISO 27001). [NIST Cybersecurity Framework]
- Employee Feedback: Collect feedback on security training and processes to identify areas for improvement.
Continuous Improvement Cycle
Adopt a “Plan-Do-Check-Act” (PDCA) cycle for your phishing defense:
- Plan: Define your security goals and strategies (e.g., reduce phishing clicks by X%).
- Do: Implement new technologies, conduct training, and update processes.
- Check: Monitor KPIs, conduct simulations, and audit controls to assess effectiveness.
- Act: Based on the “Check” phase, make adjustments, refine strategies, and address weaknesses.
This cyclical approach ensures your defenses remain agile and effective against an ever-changing threat landscape.
Conclusion: Building an Impenetrable Shield
In the relentless battle against cyber threats, phishing remains a persistent and dangerous foe for enterprises. Relying on single solutions is a recipe for disaster. To truly strengthen phishing defence, organizations must adopt a holistic, layered strategy that integrates cutting-edge technology, empowers employees through continuous training, and establishes robust incident response processes.
By investing in advanced email security, implementing MFA, fostering a security-aware culture, and regularly testing your defenses, you transform your enterprise from a potential target into a formidable fortress. Remember, cybersecurity is not a destination but a continuous journey of improvement and adaptation. Embrace this multi-faceted approach, and you’ll build the resilience needed to protect your assets, your data, and your reputation in the digital age.
Frequently Asked Questions (FAQs)
Q1: How often should phishing simulations be conducted?
At least quarterly, but monthly testing provides better behavioural insights.
Q2: Is MFA enough to stop phishing?
MFA drastically reduces the impact, but it should be part of a broader strategy involving email filters, training, and network monitoring.
Q3: Can phishing be completely prevented?
No defence is 100% foolproof, but with a layered security approach, the success rate of phishing attacks can be reduced to near-zero.














1 Comment