In today’s fast-paced digital world, businesses are moving to the cloud faster than ever. It’s like moving your entire office from a building you own to a super-secure, shared skyscraper. While the cloud offers amazing flexibility, cost savings, and innovation, it also brings new security challenges that keep Chief Information Security Officers (CISOs) awake at night.
I’ve seen firsthand how quickly the landscape changes. What was secure yesterday might be vulnerable today. As a CISO, your role isn’t just about protecting what’s inside your own walls anymore; it’s about securing your data and operations across vast, shared digital environments. This isn’t just a technical challenge; it’s a strategic one that impacts every part of your organization. We need to understand the unique risks of the cloud and put strong plans in place to handle them. This guide will walk you through the essential cloud security best practices that I believe every CISO should know and implement.
Table of Contents
Essential Insights
- Shared Responsibility is Key: Understand that cloud security is a partnership between you and your cloud provider. You’re responsible for securing your data and applications in the cloud, while they secure the cloud itself.
- Strong Identity Controls Are Crucial: Who can access what? Make sure only the right people and systems have access, using strong passwords, multi-factor authentication, and the “least privilege” rule.
- Data Protection is Paramount: Encrypt your data everywhere – whether it’s sitting still or moving around. Know where your data is and keep it safe from prying eyes.
- Continuous Monitoring is a Must: You can’t protect what you don’t see. Always watch your cloud environment for unusual activity, misconfigurations, and threats.
- Plan for the Worst, Hope for the Best: Have a clear plan for what to do if a security incident happens, and practice it regularly. This includes how you’ll respond to attacks and recover your data.
Understanding the Cloud Security Landscape
Before we dive into best practices, it’s important to grasp the fundamental nature of cloud security. It’s not just “security in the cloud” but a whole new way of thinking about protection.
The Shared Responsibility Model
Think of it like renting an apartment. The landlord (cloud provider) handles the building’s structure, plumbing, and electricity. You (the customer) are responsible for locking your doors and keeping your valuables safe.
In cloud terms:
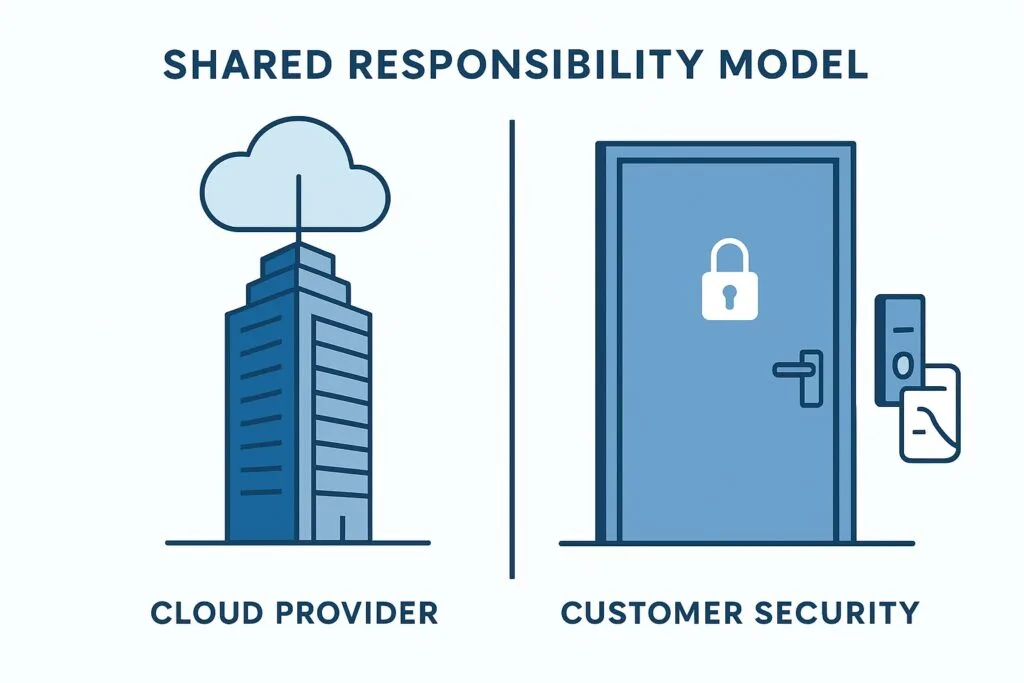
- Provider (Security of the Cloud): Secures infrastructure, networking, servers, virtualization, and data centers.
- Customer (Security in the Cloud): Secures data, applications, operating systems, network settings, and identity controls.
Most breaches happen here — not because the provider failed, but due to customer misconfigurations.
Understanding the Shared Responsibility Model is the first step toward effective cloud security. It defines where your security team must focus.
Unique Cloud Risks You Must Address
While many traditional security risks still apply, the cloud introduces specific challenges:
- Misconfigurations: This is by far the biggest culprit in cloud breaches. Easy-to-make errors in setting up cloud services can leave data exposed or systems vulnerable. Think of an open S3 bucket.
- Lack of Visibility: It can be harder to see what’s happening across your cloud environment compared to your own data center. This makes it tough to detect threats.
- Identity and Access Management (IAM) Complexity: Managing who has access to what, especially across multiple cloud services, can get very complicated, very quickly.
- Data Sprawl: Data can easily spread across different regions and services, making it hard to keep track of sensitive information.
- Shadow IT: Employees using unauthorized cloud services without IT’s knowledge creates unmanaged risks.
- API Vulnerabilities: Cloud services heavily rely on APIs. If these aren’t secured properly, they can be entry points for attackers.
- Third-Party Risk: When you use a cloud provider, you’re trusting them with your data. You also need to consider the security of any other third-party services they might use. For a deeper dive into managing these relationships, it’s vital to understand the third-party risk assessment.
Core Cloud Security Best Practices
Now, let’s get into the actionable steps. These are the cloud security best practices that I believe form the backbone of any robust cloud security strategy.
1. Robust Identity and Access Management (IAM)
This is often the first line of defense. If an attacker can pretend to be a legitimate user, they can bypass many other security controls.

- Principle of Least Privilege: Users and systems should only have the minimum permissions needed to do their job. No more, no less. This limits the damage an attacker can do if an account is compromised.
- Multi-Factor Authentication (MFA): Always, always, always enable MFA for all users, especially administrators. It adds an extra layer of security beyond just a password.
- Strong Password Policies: Enforce complex passwords and regular changes.
- Role-Based Access Control (RBAC): Group users into roles (e.g., “Developer,” “Auditor”) and assign permissions to roles, not individual users. This makes management easier and reduces errors.
- Regular Access Reviews: Periodically review who has access to what. Remove access for employees who have left or changed roles.
- Service Account Management: Securely manage credentials for applications and services, avoiding hardcoding them. Use managed identity solutions where possible.
2. Comprehensive Data Protection and Encryption
Data is the crown jewel. Protecting it is non-negotiable.

- Data Classification: Know what data you have and how sensitive it is. Not all data needs the same level of protection.
- Encryption at Rest: Encrypt data when it’s stored in cloud storage (databases, object storage). Most cloud providers offer this as a built-in feature.
- Encryption in Transit: Encrypt data as it moves between users, applications, and cloud services (e.g., using TLS/SSL).
- Data Loss Prevention (DLP): Implement DLP solutions to prevent sensitive data from leaving your cloud environment or being shared improperly.
- Data Backup and Recovery: Have a clear strategy for backing up your data and restoring it quickly in case of an incident. For a comprehensive approach, learn how to master your data protection strategy.
- Key Management: Securely manage your encryption keys. Cloud providers offer Key Management Services (KMS) that integrate well.
3. Network Security and Segmentation
Even though the cloud is “virtual,” networks still exist and need protection.
- Virtual Private Clouds (VPCs): Use VPCs or similar constructs to create isolated network environments within the public cloud.
- Network Segmentation: Divide your VPCs into smaller subnets to separate different applications or data tiers. This limits lateral movement for attackers.
- Firewalls and Security Groups: Configure virtual firewalls and security groups to control traffic flow to and from your cloud resources. Only allow necessary ports and protocols.
- Web Application Firewalls (WAFs): Protect your web applications from common attacks like SQL injection and cross-site scripting.
- DDoS Protection: Implement measures to protect against Distributed Denial of Service attacks, which can make your services unavailable.
- VPNs for Remote Access: Ensure secure remote access to your cloud resources using VPNs.
4. Vulnerability Management and Patching
Even in the cloud, software vulnerabilities can be exploited.
- Continuous Vulnerability Scanning: Regularly scan your cloud instances, containers, and applications for known vulnerabilities.
- Timely Patch Management: Apply security patches and updates promptly to operating systems, applications, and frameworks. This is a shared responsibility – your cloud provider patches their infrastructure, but you patch your guest OS and applications. Staying informed about critical vulnerabilities, such as a Fortinet zero-day vulnerability (CVE-2024-55591), is crucial for proactive defense.
- Penetration Testing: Periodically conduct authorized penetration tests to identify weaknesses in your cloud environment. Always check with your cloud provider’s policy before starting.
5. Secure Configuration Management
Misconfigurations are a CISO’s nightmare. Get them right from the start.
- Baseline Configurations: Define secure baseline configurations for all your cloud resources (VMs, storage buckets, databases, etc.).
- Infrastructure as Code (IaC): Use IaC tools (like Terraform, CloudFormation) to define your infrastructure. This makes configurations repeatable, auditable, and less prone to manual errors.
- Configuration Drift Detection: Monitor your configurations to detect unauthorized changes from your defined baselines.
- Automated Audits: Use tools to automatically check your cloud configurations against security best practices and compliance standards.
6. Robust Logging and Monitoring
You can’t protect what you don’t see. Good visibility is crucial for detecting and responding to threats.
- Centralized Logging: Collect logs from all your cloud resources (network flow logs, activity logs, application logs) into a central logging system.
- Security Information and Event Management (SIEM): Integrate your cloud logs with a SIEM solution to correlate events, detect anomalies, and generate alerts.
- Continuous Monitoring: Actively monitor for unusual activity, unauthorized access attempts, data exfiltration, and resource changes.
- Alerting and Triage: Set up effective alerts for critical security events and have a clear process for investigating and responding to them.
7. Incident Response and Recovery Planning
No matter how good your defenses, incidents can happen. Being prepared is key.

- Develop an Incident Response Plan (IRP): Create a clear, documented plan outlining steps to take before, during, and after a security incident. This includes roles, responsibilities, communication protocols, and technical procedures.
- Regular Testing: Practice your IRP through tabletop exercises and simulations. Identify gaps and refine the plan.
- Business Continuity and Disaster Recovery (BCDR): Ensure your critical cloud applications and data can be recovered quickly after a major disruption. This often involves replicating data across different regions. Learning from real-world events, such as the ICBC bank ransomware attack, can provide valuable insights for your own planning.
- Forensics Capabilities: Plan how you’ll collect and preserve evidence for forensic analysis after an incident.
8. Compliance and Governance
Meeting regulatory requirements and internal policies is a continuous effort in the cloud.
- Understand Regulatory Requirements: Know which compliance frameworks apply to your organization (e.g., GDPR, HIPAA, PCI DSS, ISO 27001).
- Cloud Compliance Tools: Leverage cloud provider tools and third-party solutions that help automate compliance checks and generate reports.
- Policy Enforcement: Ensure your cloud security policies are clearly defined, communicated, and enforced across your organization.
- Regular Audits: Conduct internal and external audits to verify compliance with regulations and your own security policies.
- Data Residency: Understand where your data is stored geographically, especially for global operations, to comply with data residency laws.
9. Third-Party Risk Management
Your cloud provider is a third party, but so are the many other services and tools you might integrate.
- Vendor Assessment: Thoroughly assess the security posture of all cloud providers and third-party services you use.
- Contractual Agreements: Ensure your contracts clearly define security responsibilities, data ownership, incident notification, and audit rights.
- Supply Chain Security: Extend your risk assessment beyond direct providers to their own supply chain if possible.
- Continuous Monitoring of Third Parties: Don’t just set it and forget it. Continuously monitor your third-party vendors for security incidents or changes in their posture. Recent events, like Oracle confirming a data breach in legacy cloud systems, highlight the ongoing need for vigilance even with major providers.
10. Security Awareness and Training
Your employees are often your strongest or weakest link.

- Regular Training: Educate all employees, from executives to new hires, about cloud security risks, best practices, and their role in protecting data.
- Phishing Simulations: Conduct regular phishing simulations to train employees to recognize and report suspicious emails.
- Role-Specific Training: Provide specialized training for developers, operations teams, and IT staff on secure cloud development and operations.
- Culture of Security: Foster a culture where security is everyone’s responsibility, not just the security team’s. This foundational understanding of information security and its role in cybersecurity is critical for building a strong security culture.
Advanced Cloud Security Strategies
Beyond the core practices, CISOs should also explore more advanced strategies to enhance their cloud defenses.
DevSecOps Integration
Shift security left! Integrating security into every stage of the development pipeline (design, code, build, test, deploy) helps catch vulnerabilities early when they’re cheaper and easier to fix. This means automating security checks, using secure coding practices, and embedding security tools into CI/CD pipelines.
Cloud Security Posture Management (CSPM)
CSPM tools continuously monitor your cloud environment for misconfigurations, compliance violations, and security risks. They provide a unified view across multiple cloud providers and help automate remediation. Think of it as an automated security auditor constantly checking your cloud settings.
Cloud Workload Protection Platforms (CWPP)
CWPPs focus on protecting workloads (virtual machines, containers, serverless functions) running in the cloud. They offer features like vulnerability management, runtime protection, application control, and micro-segmentation to secure your compute resources.
AI and Machine Learning in Security
AI and ML are becoming indispensable for detecting complex threats that human analysts might miss. They can analyze vast amounts of log data, identify unusual patterns, predict attacks, and automate responses. CISOs need to consider how AI will impact the CISO role in 2025 and beyond, as these technologies evolve.
The Evolving Role of the CISO in Cloud Security
The CISO’s role in the cloud era is no longer purely technical. It’s strategic, communicative, and visionary.
- Strategic Leadership: You need to align cloud security with business goals, articulate risks to the board, and secure necessary resources.
- Risk Management: Focus on identifying, assessing, and mitigating cloud-specific risks, understanding that the cloud changes the risk profile significantly.
- Collaboration: Work closely with development teams (DevSecOps), operations, legal, and compliance departments. Cloud security is a team sport!
- Vendor Management: Act as a key stakeholder in selecting and managing cloud providers and security vendors.
- Continuous Learning: The cloud evolves rapidly. Stay updated on new services, threats, and security solutions.
As CISOs, we must be proactive, not reactive. The cloud demands continuous improvement and adaptation.
The Bottom Line: Securing Your Cloud Future
Embracing the cloud offers incredible benefits, but it also elevates the importance of robust security practices. As CISOs, it’s our duty to not only understand these cloud security best practices but to champion their implementation across our organizations. By focusing on strong identity controls, comprehensive data protection, vigilant monitoring, and proactive incident response, we can build secure cloud environments that support innovation without compromising trust.
Remember, cloud security is not a one-time project; it’s an ongoing journey. Stay informed, stay vigilant, and empower your teams with the knowledge and tools they need to protect your digital assets in the ever-expanding cloud frontier. Your organization’s future depends on it.












Leave a comment