Awareness
Boost your awareness with insights, guides, and real-world examples that highlight common risks, best practices, and smart ways to stay safe and informed.
The Hidden Costs of Ransomware Attack on Your Business
In the heat of a ransomware attack, businesses often face a single agonising question: should we pay the ransom? But the ransom demand...
ByKumar SJuly 2, 2025A Practical Guide to Phishing Awareness for Employees
In today’s digital-first business landscape, phishing is more than just a nuisance—it’s a serious threat to your finances, your reputation, and your data....
ByKumar SJune 30, 2025Importance of Network Segmentation in Modern Cybersecurity
In today’s threat landscape, assuming your internal network is secure just because it sits behind a firewall is a dangerous fallacy. Cybercriminals are...
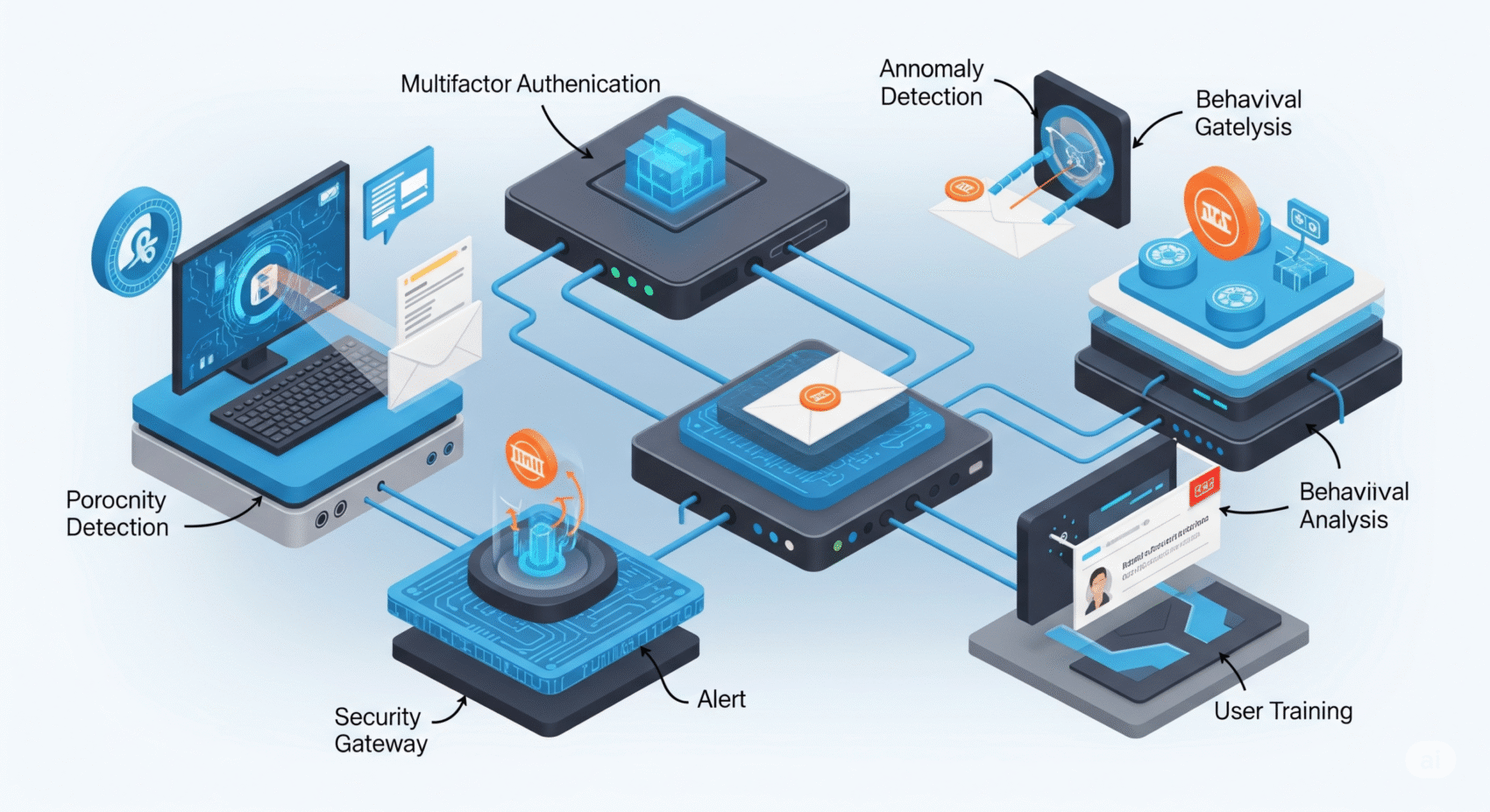
ByKumar SJune 3, 2025Strengthen Phishing Defence Mechanisms: Practical, Layered Protection for Enterprise
In today’s fast-paced digital world, businesses face a constant barrage of cyber threats. Among these, phishing attacks stand out as one of the...
ByKumar SJune 3, 2025Cyberwarfare in the Age of AI: New Weapons, New Rules
Artificial intelligence is transforming cyberwarfare, enabling faster, stealthier, and more destructive digital attacks. From autonomous malware to deepfake-driven misinformation, nations face new threats...
ByKumar SMay 20, 2025What is Digital Arrest? Shocking Facts Behind This Alarming Online Scam
"Digital Arrest” is a terrifying new cyber scam where criminals impersonate police or government officials and psychologically trap victims into paying money to...
ByKumar SApril 30, 2025How to Create a Secure BYOD Policy | BYOD Security Best Practices
Learn how to implement a secure BYOD policy without compromising data security. Best practices, key steps, and future trends for safe BYOD adoption.
ByKumar SApril 28, 2025Inbox Overload? Sorting Through the Aggravation of Spam vs Phishing
Understanding the difference isn’t just about cleaning your inbox. Let's understand Spam vs Phishing
ByKumar SApril 25, 2025