Here’s a shocking reality: 60% of small businesses close within six months of experiencing a cyber attack. Yet, according to recent studies, only 14% of companies are fully prepared to defend against cybersecurity threats! This alarming gap between risk and preparedness makes cyber risk assessment not just important – it’s absolutely critical for business survival in 2025.
If you’re a business owner or IT professional wondering where to start with cybersecurity, you’ve come to the right place. I’ve guided hundreds of organizations through comprehensive cyber risk assessments, and I can tell you that the process doesn’t have to be overwhelming or impossibly complex. With the right approach, you can systematically identify your vulnerabilities, understand your exposure, and build a roadmap for meaningful security improvements.
Table of Contents
Whether you’re running a small startup or managing enterprise security, this guide will walk you through every step of conducting a thorough cyber risk assessment. By the end, you’ll have the knowledge and tools needed to protect your business from the ever-evolving landscape of cyber threats. Let’s dive in!
Understanding How to Conduct a Cyber Risk Assessment for Your Business
A cyber risk assessment is essentially a systematic evaluation of your organization’s cybersecurity posture. Think of it as a comprehensive health checkup for your digital infrastructure. The goal isn’t to achieve perfect security – that’s impossible – but to understand your risks well enough to make informed decisions about where to invest your limited security resources.
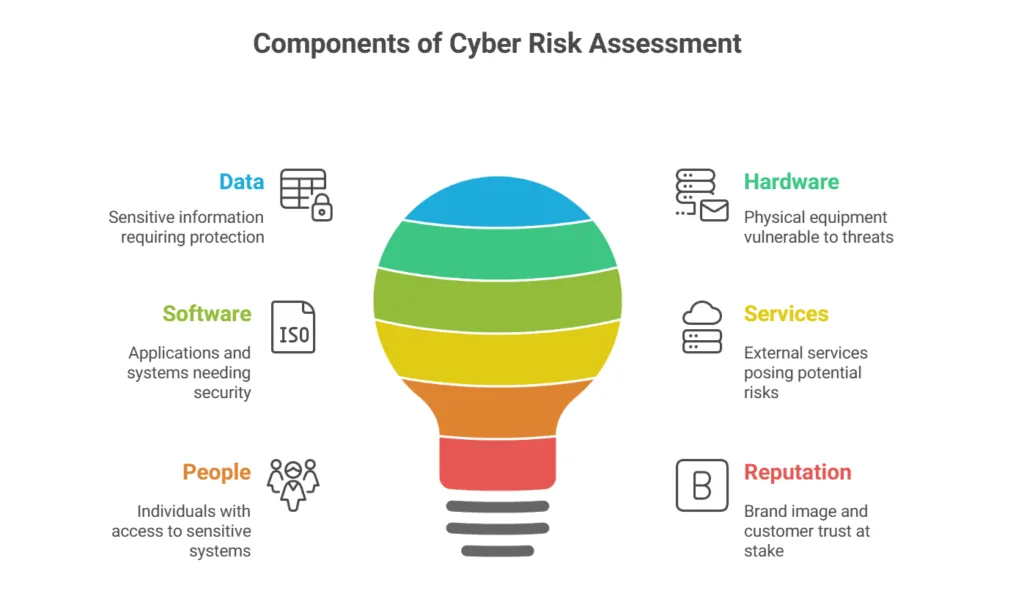
Risk assessment differs from vulnerability scanning in several important ways. While vulnerability scans identify technical weaknesses in your systems, risk assessments consider the broader business context. They evaluate not just what could go wrong, but how likely it is to happen and what the business impact would be if it did.
The process involves three fundamental components: assets, threats, and vulnerabilities. Assets are anything of value to your organization – data, systems, people, and reputation. Threats are potential dangers that could harm these assets, ranging from cybercriminals and insider threats to natural disasters and system failures. Vulnerabilities are weaknesses that threats could exploit to cause damage.
Modern cyber risk assessment frameworks have evolved beyond simple checklists. They now incorporate threat intelligence, business impact analysis, and dynamic risk scoring that can adapt as your organization and the threat landscape change. The most effective assessments consider both technical risks and business risks, understanding that a minor technical vulnerability in a critical system might pose greater risk than a major vulnerability in a less important system.
Regulatory compliance often drives risk assessment requirements, but smart organizations go beyond minimum compliance standards. Frameworks like NIST, ISO 27001, and industry-specific standards provide excellent starting points, but your assessment should be tailored to your specific business model, industry, and risk tolerance. Understanding the latest cybersecurity trends and threats helps ensure your assessment addresses current and emerging risks.
Business stakeholder involvement is crucial for effective risk assessment. IT teams understand technical vulnerabilities, but business leaders understand operational impact, regulatory requirements, and acceptable risk levels. The most successful assessments bring these perspectives together to create a comprehensive view of organizational risk.
Preparing for Your Cyber Risk Assessment
Proper preparation sets the foundation for a successful risk assessment. Without adequate planning, you’ll likely miss critical assets, underestimate threats, or fail to engage the right stakeholders. Take time to establish clear objectives and gather the necessary resources before diving into the technical evaluation.
Define your assessment scope and objectives clearly from the start. Are you conducting a comprehensive organizational assessment, focusing on a specific system or process, or preparing for regulatory compliance? Different objectives require different approaches and levels of detail. Document your scope to ensure all stakeholders understand what will and won’t be included.
Assemble your assessment team with representatives from IT, security, business operations, legal, and senior management. Each group brings unique perspectives and expertise that contribute to a more comprehensive evaluation. Designate a project leader who can coordinate activities and ensure the assessment stays on track.
Gather preliminary documentation including network diagrams, asset inventories, existing security policies, previous audit reports, and incident histories. This background information helps the assessment team understand your current security posture and identify areas requiring deeper investigation.
Establish assessment criteria and risk tolerance levels before beginning the evaluation. What constitutes high, medium, and low risk for your organization? How do you balance security investments against other business priorities? Having these discussions upfront prevents confusion and disagreement later in the process.
Plan your assessment timeline realistically, accounting for the time needed to inventory assets, conduct interviews, perform technical testing, and analyze results. Most comprehensive assessments take several weeks to complete, depending on organizational size and complexity. Build in time for stakeholder review and remediation planning.
Consider external expertise if your internal team lacks risk assessment experience. Professional cybersecurity consultants bring specialized knowledge, objective perspectives, and proven methodologies. They can also provide credibility when presenting findings to senior leadership or external stakeholders.
Asset Identification and Classification
You can’t protect what you don’t know you have. Asset identification forms the cornerstone of effective risk assessment, yet many organizations struggle with this fundamental step. Today’s complex IT environments, with cloud services, mobile devices, and shadow IT, make comprehensive asset discovery more challenging than ever.
Start with a comprehensive asset inventory that goes beyond traditional IT assets. Include physical devices like computers, servers, and network equipment, but don’t forget about virtual assets like cloud instances, containers, and software-as-a-service applications. Document mobile devices, IoT sensors, and any other connected equipment that could provide attack vectors.
Data assets require special attention because they’re often your organization’s most valuable and vulnerable resources. Catalog databases, file shares, cloud storage repositories, and any systems that process, store, or transmit sensitive information. Don’t overlook data in transit, backups, archives, and copies that might exist on employee devices or in shadow IT systems.
Classification systems help prioritize protection efforts by categorizing assets based on their importance to business operations, sensitivity of data they contain, and potential impact if compromised. Common classification schemes use labels like Critical, High, Medium, and Low, but develop criteria that make sense for your organization’s specific context.
Critical assets typically include systems that directly support revenue generation, contain highly sensitive data, or are required for essential business operations. These might include customer databases, financial systems, manufacturing control systems, or e-commerce platforms. Loss or compromise of critical assets could threaten business survival or result in significant regulatory penalties.
Asset relationships and dependencies are just as important as individual assets. Map how systems connect to and depend on each other, identifying single points of failure and cascading risk scenarios. A seemingly minor system might be critical if many other systems depend on it, while a high-value system might be lower risk if it’s well-isolated from other network resources.
Dynamic asset management acknowledges that modern IT environments change constantly. Implement processes for discovering new assets, tracking changes to existing assets, and removing decommissioned systems from your inventory. Automated discovery tools can help, but they need regular updates and manual verification to ensure accuracy.
Threat Identification and Analysis
Understanding your threat landscape is essential for realistic risk assessment. Not all organizations face the same threats, and generic threat lists often miss industry-specific or organization-specific risks that could have the greatest impact on your business.
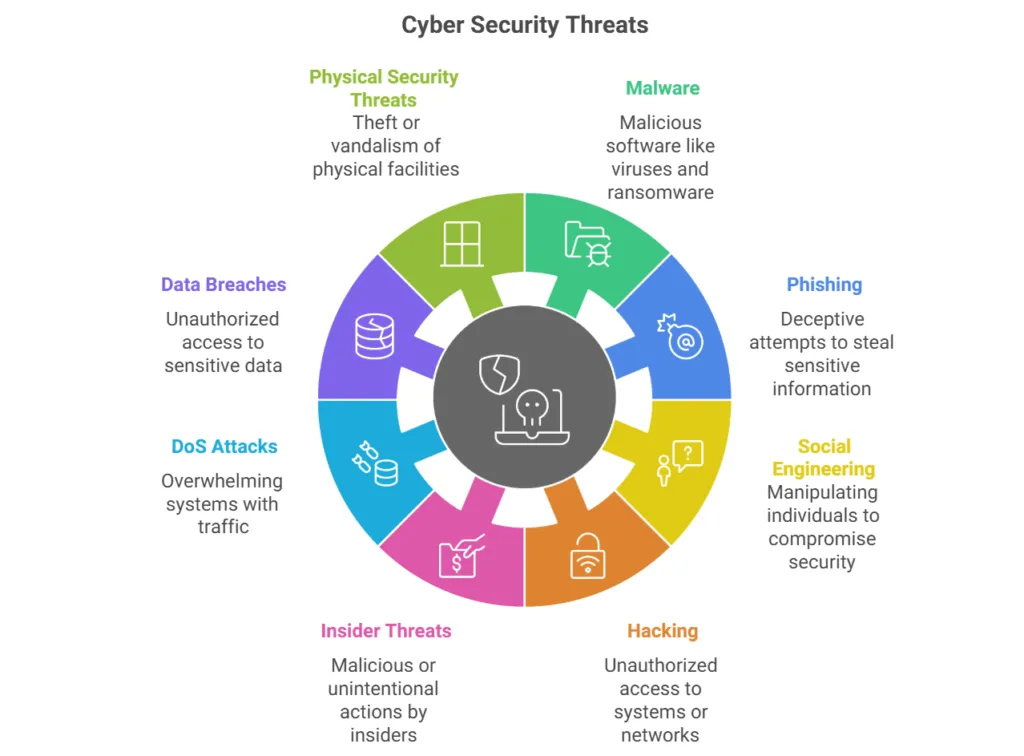
Threat actors vary dramatically in their motivations, capabilities, and targeting preferences. Cybercriminals seek financial gain through ransomware, fraud, or data theft. Nation-state actors pursue espionage, sabotage, or strategic advantage. Insider threats might involve malicious employees, compromised accounts, or simply human error. Understanding who might target your organization helps focus your defensive efforts.
Attack vectors represent the methods threats use to compromise your assets. Traditional vectors like malware and phishing remain popular, but attackers increasingly exploit cloud misconfigurations, supply chain relationships, and social engineering techniques. Stay current with evolving attack methods by monitoring major cyber attacks and incidents that affect organizations similar to yours.
Industry-specific threats require special consideration. Healthcare organizations face different risks than financial institutions or manufacturing companies. Regulatory requirements, data types, operational technologies, and attacker interests vary significantly across industries. Research threats that have specifically targeted your industry and understand how they might apply to your organization.
Threat intelligence provides valuable context for understanding current and emerging threats. Commercial threat intelligence feeds offer structured data about indicators of compromise, attack campaigns, and threat actor behaviors. Free resources like government advisories and security vendor reports also provide useful insights for threat identification.
Environmental threats extend beyond cybercriminals to include natural disasters, power outages, hardware failures, and other events that could disrupt operations or compromise security controls. While these might seem outside the scope of cybersecurity, they often create conditions that increase cyber risk or interfere with incident response capabilities.
Insider threat assessment deserves particular attention because internal threats can be especially damaging and difficult to detect. Consider risks from current employees with elevated privileges, former employees who might retain access, contractors and vendors with system access, and the potential for social engineering or account compromise that could turn legitimate users into unwitting threats.
Vulnerability Assessment Methodology
Identifying vulnerabilities requires a systematic approach that combines automated scanning with manual testing and analysis. The goal is to understand not just what vulnerabilities exist, but how they could be exploited and what business impact might result.
Automated vulnerability scanning provides broad coverage and consistency in identifying known security flaws. Deploy scanners that can assess network infrastructure, web applications, databases, and endpoint systems. Schedule regular scans to catch new vulnerabilities as they’re discovered, but remember that scanners only identify known issues and can miss custom applications, configuration problems, or complex attack chains.
Network vulnerability assessment examines your network infrastructure for weaknesses that could enable unauthorized access or lateral movement. This includes evaluating firewall configurations, network segmentation, wireless security, remote access solutions, and network device security settings. Pay special attention to perimeter security and internal network controls that could limit damage from successful breaches.
Application security testing addresses vulnerabilities in custom and commercial software applications. Web application scanning identifies common flaws like injection attacks, authentication bypasses, and cross-site scripting vulnerabilities. Source code analysis can find deeper security issues in custom applications, while configuration reviews ensure that commercial applications are properly secured.
Configuration management assessment evaluates whether systems are configured according to security best practices. This includes operating system hardening, database security settings, cloud service configurations, and security tool deployments. Configuration vulnerabilities are often easier to exploit than software bugs and may not be detected by traditional vulnerability scanners.
Physical security evaluation examines controls that protect against physical threats and unauthorized facility access. While often overlooked in cyber risk assessments, physical security weaknesses can enable attackers to bypass network security controls entirely. Assess facility access controls, equipment security, and policies for handling sensitive information and devices.
Social engineering susceptibility testing evaluates how well your employees resist manipulation attempts. This might include simulated phishing campaigns, pretexting exercises, or physical social engineering tests. Human vulnerabilities can be the easiest attack vector for sophisticated threat actors, making security awareness training and testing crucial components of vulnerability assessment.
Risk Analysis and Prioritization
Once you’ve identified assets, threats, and vulnerabilities, the next step is analyzing how these elements interact to create risk. This analysis transforms technical findings into business-relevant information that can guide decision-making and resource allocation.
Risk calculation methodology typically involves evaluating the likelihood of threat exploitation against the potential business impact. Common approaches use qualitative scales (High/Medium/Low) or quantitative models that assign numerical values to probability and impact factors. Choose a methodology that matches your organization’s sophistication and provides useful decision-making information.
Likelihood assessment considers factors like threat actor motivation and capability, vulnerability exploitability, and existing security controls. A critical vulnerability in an internet-facing system targeted by active threat campaigns represents higher likelihood than a similar vulnerability in an isolated internal system. Threat intelligence and historical attack data can inform likelihood estimates.
Impact analysis evaluates potential business consequences if risks are realized. Consider direct costs like incident response and system recovery, indirect costs like business disruption and reputation damage, and regulatory consequences like fines and legal liability. Impact assessment should account for both immediate effects and longer-term business implications.
Risk scoring and ranking helps prioritize remediation efforts by combining likelihood and impact assessments. Develop scoring criteria that reflect your organization’s risk tolerance and business priorities. Remember that mathematical precision isn’t the goal – you need rankings that help make reasonable decisions about where to invest limited security resources.
Business context integration ensures that risk analysis considers operational realities, not just technical factors. A high-risk vulnerability in a system scheduled for replacement next month might receive lower priority than a medium-risk issue in a critical production system. Include business stakeholders in risk prioritization discussions to ensure technical assessments align with business needs.
Risk heat maps and visualization help communicate findings to stakeholders who might not understand technical details. Visual representations of risk across different business areas, asset types, or threat categories can highlight patterns and priorities that might not be obvious from spreadsheet listings. Effective visualization makes risk assessment results actionable for decision-makers.
Compliance and Regulatory Considerations
Regulatory compliance adds another layer of complexity to cyber risk assessment, but it also provides valuable frameworks and requirements that can strengthen your overall security posture. Understanding applicable regulations helps ensure your assessment addresses all necessary requirements while avoiding redundant efforts.
Industry-specific regulations vary significantly in their requirements and focus areas. Healthcare organizations must consider HIPAA requirements, financial institutions face regulations like PCI DSS and SOX, and government contractors must address NIST and FISMA requirements. Research regulations that apply to your industry and ensure your risk assessment addresses their specific requirements.
Data protection regulations like GDPR, CCPA, and similar laws impose requirements for protecting personal information and reporting data breaches. These regulations often require organizations to conduct regular risk assessments and implement appropriate technical and organizational measures to protect personal data. Document how your risk assessment addresses these requirements.
Compliance framework alignment can streamline both risk assessment and ongoing security management. Frameworks like NIST Cybersecurity Framework, ISO 27001, and CIS Controls provide structured approaches to cybersecurity that satisfy many regulatory requirements. Aligning your risk assessment with established frameworks can simplify compliance reporting and security program management.
Third-party compliance requirements extend your compliance obligations to vendors, partners, and service providers who handle your data or have access to your systems. Assess whether your suppliers meet relevant compliance standards and understand how their security practices affect your overall risk posture. Contract terms should address security requirements and incident notification procedures.
Audit and reporting requirements vary by regulation but typically include documentation of risk assessment processes, findings, and remediation efforts. Maintain detailed records of your assessment methodology, stakeholder involvement, and management responses to identified risks. This documentation supports compliance audits and demonstrates due diligence in risk management.
International compliance considerations become important for organizations operating across multiple jurisdictions. Different countries and regions have varying cybersecurity and data protection requirements that might conflict with each other. Understanding the complex landscape of global cybersecurity regulations helps ensure your risk assessment addresses all applicable requirements.
Risk Treatment and Mitigation Strategies
Identifying risks is only valuable if you act on the findings. Risk treatment involves deciding how to address each identified risk through mitigation, acceptance, transfer, or avoidance strategies. The goal is to reduce overall risk to acceptable levels while making efficient use of available resources.
Risk mitigation involves implementing controls to reduce either the likelihood of risk realization or its potential impact. Technical controls like firewalls, encryption, and access management systems directly address vulnerabilities, while administrative controls like policies and training reduce the likelihood of human error or insider threats. Physical controls protect against unauthorized facility access and environmental hazards.
Risk acceptance might be appropriate for low-impact risks or situations where mitigation costs exceed potential damages. Document accepted risks clearly, including the rationale for acceptance and any conditions that might trigger future action. Senior management should formally approve risk acceptance decisions, especially for risks that could have significant business impact.
Risk transfer strategies shift risk to other parties through insurance, contracts, or service agreements. Cyber insurance can help cover costs associated with data breaches and business interruption, while contracts with vendors can transfer certain risks to service providers. However, risk transfer doesn’t eliminate your underlying vulnerabilities or compliance obligations.
Risk avoidance involves eliminating activities or assets that create unacceptable risk. This might mean discontinuing certain business activities, retiring vulnerable systems, or avoiding technologies that present excessive risk. While avoidance can be effective, it’s often impractical for risks related to core business functions.
Control effectiveness assessment ensures that implemented risk treatments actually reduce risk as intended. Monitor key security metrics, conduct regular testing of security controls, and validate that mitigation measures continue to address identified risks. Risk treatment is an ongoing process, not a one-time implementation.
Cost-benefit analysis helps optimize resource allocation by comparing the cost of risk treatment options against their expected risk reduction benefits. Consider both direct costs like technology purchases and implementation services, and indirect costs like ongoing maintenance, user productivity impacts, and operational complexity. Sometimes the most expensive option provides the best overall value.
Tools and Technologies for Risk Assessment
Modern cyber risk assessment benefits from a variety of tools and technologies that can automate data collection, standardize analysis, and improve the accuracy of findings. However, tools are only as effective as the expertise and processes behind them.
Governance, Risk, and Compliance (GRC) platforms provide integrated environments for managing risk assessments, tracking remediation efforts, and reporting to stakeholders. These platforms often include risk assessment templates, workflow management, and dashboard capabilities that streamline the assessment process. Popular GRC solutions include ServiceNow GRC, RSA Archer, and Lockpath.
Vulnerability management tools automate the discovery and assessment of technical vulnerabilities across your IT environment. Enterprise solutions like Tenable Nessus, Qualys VMDR, and Rapid7 InsightVM can scan networks, applications, and cloud environments to identify security flaws. These tools also provide prioritization features that consider exploit availability and business context.
Asset discovery and inventory tools help maintain accurate inventories of IT assets across hybrid and multi-cloud environments. Solutions like Lansweeper, ManageEngine AssetExplorer, and cloud-native tools can automatically discover devices, software, and services while tracking changes over time. Accurate asset inventory is fundamental to effective risk assessment.
Threat intelligence platforms aggregate and analyze threat data from multiple sources to provide context for risk assessment. Commercial platforms like Recorded Future, ThreatConnect, and Anomali offer structured threat intelligence that can inform risk likelihood assessments and help prioritize vulnerabilities based on active threats.
Security assessment frameworks provide structured methodologies for conducting risk assessments. The NIST Cybersecurity Framework offers a comprehensive approach that many organizations find practical and effective. FAIR (Factor Analysis of Information Risk) provides a more quantitative approach for organizations that need detailed risk calculations.
Cloud security assessment tools address the unique challenges of assessing risk in cloud environments. Tools like Prowler for AWS, Scout Suite for multi-cloud environments, and cloud-native security services help identify misconfigurations and compliance violations that create security risks. As more organizations adopt cloud security best practices, these tools become increasingly important.
Creating Your Risk Assessment Report
A well-structured risk assessment report translates technical findings into actionable business intelligence that can guide security investments and strategic decision-making. The report should serve multiple audiences, from technical teams who will implement remediation measures to executive leadership who need to understand business implications.
Executive summary provides high-level findings and recommendations for senior leadership who might not read the detailed technical sections. Focus on business impact, overall risk posture, and strategic recommendations rather than technical details. Include key metrics like the number of critical risks identified, progress since previous assessments, and recommended investment levels.
Methodology section documents your assessment approach, scope, and limitations to provide context for findings and support reproducibility for future assessments. Include information about assessment team composition, timeframes, tools used, and any constraints that might have affected the evaluation. This section supports the credibility of your findings and helps readers understand any limitations.
Asset inventory and classification results should summarize your findings about organizational assets, their classification levels, and any significant discoveries made during the inventory process. Highlight critical assets, newly discovered systems, and any assets that weren’t properly classified or protected according to their importance.
Risk findings form the core of your report and should present identified risks in order of priority, with clear descriptions of threat scenarios, affected assets, and potential business impacts. Use consistent risk scoring and categorization throughout the report to enable comparison and prioritization. Include enough technical detail to support remediation planning without overwhelming non-technical readers.
Remediation recommendations should provide specific, actionable guidance for addressing identified risks. Organize recommendations by priority level and include estimated costs, implementation timeframes, and resource requirements. Consider both immediate tactical fixes and longer-term strategic improvements to security posture.
Compliance assessment results should clearly document how current security posture aligns with applicable regulatory requirements and industry standards. Identify specific compliance gaps, required remediation actions, and timelines for achieving compliance. This section is particularly important for organizations subject to regulatory oversight.
Implementing Continuous Risk Management
Cyber risk assessment shouldn’t be a once-per-year activity filed away until the next annual review. Effective risk management requires ongoing monitoring, regular reassessment, and adaptive responses to changing threats and business conditions.
Continuous monitoring programs track key risk indicators and security metrics to identify changes in risk posture between formal assessments. This might include vulnerability scan results, security incident trends, threat intelligence feeds, and compliance monitoring data. Automated monitoring tools can alert you to significant changes that might require immediate attention.
Regular reassessment scheduling ensures that risk evaluations remain current and relevant. Many organizations conduct comprehensive assessments annually with focused updates quarterly or after significant changes to business operations or IT infrastructure. Critical systems and high-risk areas might warrant more frequent evaluation.
Change management integration incorporates risk considerations into business change processes so that new technologies, processes, or business activities are evaluated for security implications before implementation. This proactive approach prevents the introduction of new risks and ensures that security controls keep pace with business evolution.
Risk governance processes establish clear roles, responsibilities, and decision-making authorities for ongoing risk management. Define who can accept different levels of risk, how remediation priorities are established, and how risk management activities are funded and resourced. Effective governance ensures that risk management remains a business priority rather than just an IT activity.
Metrics and reporting programs provide ongoing visibility into risk management effectiveness and help justify security investments. Track metrics like mean time to remediation, percentage of high-risk items addressed, and trends in overall risk exposure. Regular reporting to senior leadership maintains awareness and support for risk management activities.
Incident response integration connects risk assessment findings with incident response planning and execution. Use risk assessment results to prioritize incident response planning efforts, and incorporate lessons learned from security incidents into future risk assessments. This integration ensures that theoretical risk assessments remain grounded in operational realities.
The Bottom Line
Conducting a comprehensive cyber risk assessment might seem daunting, but it’s one of the most valuable investments you can make in your organization’s security and resilience. The process we’ve outlined provides a systematic approach to understanding your unique risk landscape and making informed decisions about cybersecurity investments.
Remember, the goal isn’t to achieve perfect security – that’s neither possible nor economically viable. Instead, you’re working to understand your risks well enough to manage them effectively within your business constraints and risk tolerance. A well-executed risk assessment provides the foundation for all other cybersecurity activities and helps ensure that your limited security resources are focused on the areas that matter most.
The threat landscape will continue evolving, and your risk profile will change as your business grows and adapts. Make risk assessment an ongoing process rather than a one-time project. Regular reassessment and continuous monitoring will help you stay ahead of emerging threats and maintain an appropriate security posture.
Don’t let the complexity of cyber risk assessment prevent you from getting started. Begin with a focused assessment of your most critical assets and threats, then expand your scope as you gain experience and confidence with the process. Even a basic risk assessment provides valuable insights that can significantly improve your security posture.
The time to begin is now. Cyber threats won’t wait for you to be perfectly prepared, and every day of delay potentially exposes your organization to preventable risks. Start your cyber risk assessment today, and take the first step toward building a more secure and resilient business for the future.














Leave a comment