Definitions
Social Engineering: Understanding, Preventing, and Mitigating
Social engineering is one of the most insidious and pervasive threats in the cybersecurity landscape. Unlike traditional cyberattacks that exploit technical vulnerabilities, social...
ByCyberTech Journalsअप्रैल 9, 2025Understanding and Mitigating Insider Threats in 2025: A Comprehensive Guide
Discover how to identify, prevent, and respond to insider threats in 2025. Learn actionable strategies and best practices to protect your organization from...
ByKumar Sअप्रैल 8, 2025Understand Vulnerability in Cybersecurity: A Detailed Guide
In the ever-evolving landscape of cybersecurity, the term vulnerability often surfaces as a critical concept. A Vulnerability in Cybersecurity refers to a weakness...
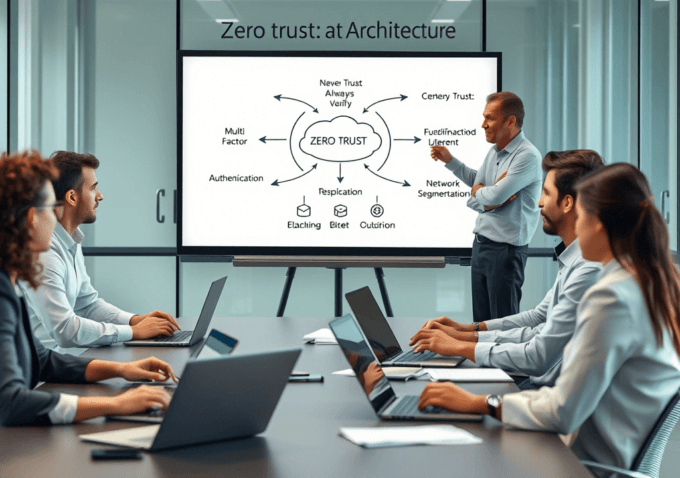
ByKumar Sअप्रैल 4, 2025What is Zero Trust Architecture? A Comprehensive Guide for 2025
In an era where cyber threats are becoming increasingly sophisticated, traditional security models that rely on perimeter-based defenses are no longer sufficient. What...
ByKumar Sफ़रवरी 17, 2025What is Malware and How Can You Protect Yourself from It?
In today’s world, where nearly everything is online, cybersecurity is more important than ever. One of the most significant threats to our digital...
ByKumar Sजनवरी 11, 2025What Is Ransomware and How Does It Work?
In today’s digital landscape, ransomware has emerged as one of the most pervasive and destructive forms of cybercrime. This malicious software encrypts a...
ByKumar Sजनवरी 6, 2025Understand Information Security and Its Role in Cybersecurity
In today’s hyper-connected world, where nearly every aspect of our lives is linked to the internet, safeguarding sensitive information is more important than...
ByKumar Sजनवरी 5, 2025Mastering Network Security in Cybersecurity with Top 7 Strategies
In the current interconnected world, network security has become a vital aspect for organizations, rather than just being a concern for IT departments....
ByKumar Sजनवरी 5, 2025