In an era where cyber threats are becoming increasingly sophisticated, traditional security models that rely on perimeter-based defenses are no longer sufficient. What is Zero Trust Architecture (ZTA)—a revolutionary approach to cybersecurity that challenges the conventional “trust but verify” mindset. As organizations adopt hybrid work environments and cloud-based systems, Zero Trust has emerged as a critical framework for ensuring robust protection of sensitive data and resources. But what exactly is Zero Trust Architecture, and why is it gaining so much attention? Let’s explore.
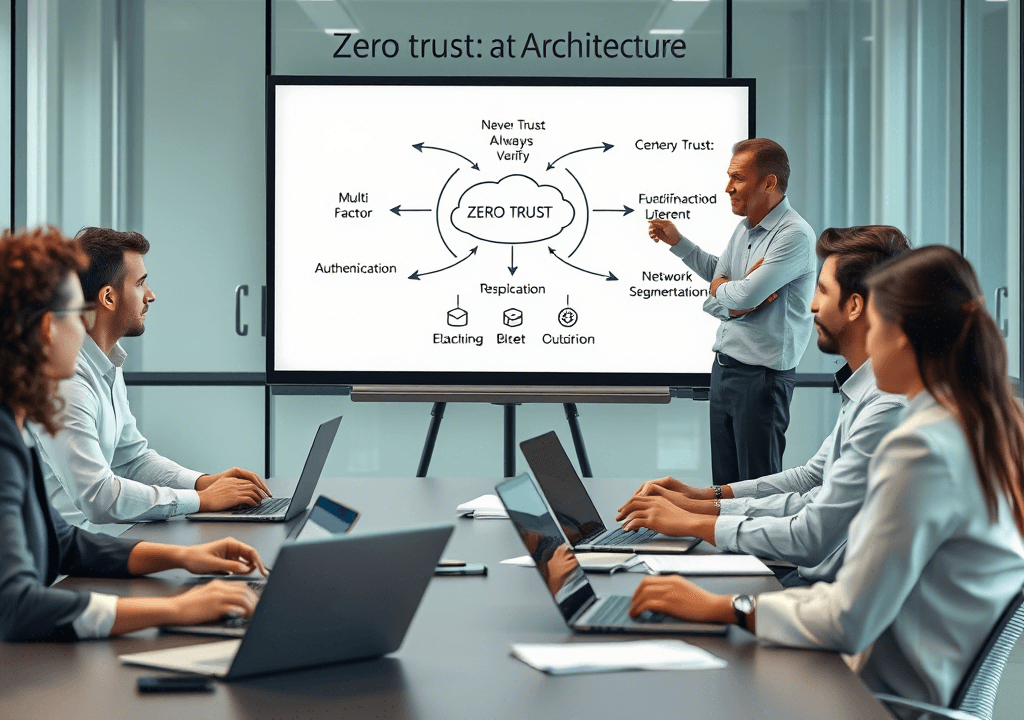
The Core Principle: “Never Trust, Always Verify”
At its heart, Zero Trust Architecture operates on the principle of “never trust, always verify.” Unlike traditional security models that assume everything inside a corporate network is safe, Zero Trust assumes that threats can come from both outside and inside the network. This means no user, device, or application is automatically trusted—even if they have previously been granted access.
Every request for access to resources is rigorously authenticated, authorized, and continuously validated before granting permissions. This approach minimizes the attack surface, limits lateral movement within networks, and ensures that only legitimate users and devices can interact with critical assets.
For more details, refer to NIST’s Zero Trust Framework.
Key Components of Zero Trust Architecture
1. Continuous Verification
Zero Trust requires ongoing validation of user identity, device health, and access privileges. Even after initial authentication, systems constantly monitor behavior to detect anomalies that could indicate a breach. For example, if an employee logs in from an unusual location or attempts to access unauthorized data, their session may be flagged or terminated.
2. Least Privilege Access
Under Zero Trust, users and devices are granted the minimum level of access necessary to perform their tasks. This reduces the risk of overexposure and limits the damage caused by compromised accounts or insider threats.
3. Micro-Segmentation
Networks are divided into smaller, isolated segments using micro-segmentation. Each segment contains specific resources, and access is tightly controlled. This prevents attackers from moving freely across the network if they manage to infiltrate one segment.
4. Multi-Factor Authentication (MFA)
MFA is a cornerstone of Zero Trust, requiring users to provide multiple forms of verification (e.g., passwords, biometrics, or one-time codes) to prove their identity. This adds an extra layer of security beyond just usernames and passwords.
5. Real-Time Monitoring and Analytics
Zero Trust leverages advanced tools like AI and machine learning to monitor activity in real time. These systems analyze patterns, detect suspicious behavior, and respond to potential threats instantly.
Why Organizations Are Adopting Zero Trust
The shift toward Zero Trust Architecture is driven by several factors:
1. Rising Cyber Threats
With ransomware, phishing, and insider attacks on the rise, organizations need stronger defenses. Zero Trust minimizes vulnerabilities by assuming breaches will happen and preparing accordingly.
2. Remote Work Revolution
The widespread adoption of remote and hybrid work has expanded the attack surface. Employees accessing corporate resources from unsecured networks necessitates a more stringent security model.
3. Cloud Migration
As businesses move to cloud environments, traditional perimeter-based security becomes obsolete. Zero Trust provides a unified framework for securing distributed systems and applications.
4. Regulatory Compliance
Many industries now require stricter security measures to comply with regulations like GDPR, HIPAA, and CCPA. Zero Trust helps organizations meet these requirements by implementing granular controls and audit trails.
For insights into regulatory alignment, visit CISA’s Zero Trust Guidance.
Benefits of Zero Trust Architecture
- Enhanced Security Posture
By eliminating implicit trust and enforcing strict access controls, Zero Trust significantly reduces the risk of breaches. - Improved Incident Response
Continuous monitoring and automated responses enable faster detection and mitigation of threats. - Scalability Across Environments
Whether you’re managing on-premises servers, cloud services, or hybrid setups, Zero Trust adapts seamlessly to diverse infrastructures. - Reduced Insider Threats
Limiting access based on roles and responsibilities curbs accidental or malicious misuse of privileges. - Cost Efficiency
While initial implementation may involve investment, Zero Trust ultimately lowers costs by preventing costly breaches and streamlining security operations.
Challenges of Implementing Zero Trust
Despite its advantages, adopting Zero Trust comes with challenges:
- Complexity: Transitioning from legacy systems to a Zero Trust model requires careful planning and integration.
- Resistance to Change: Employees and stakeholders may resist new workflows or additional authentication steps.
- Resource Intensity: Deploying technologies like MFA, micro-segmentation, and AI-driven analytics demands significant resources.
To overcome these hurdles, organizations should adopt a phased approach, starting with high-risk areas and gradually expanding coverage.
For implementation strategies, check out Microsoft’s Zero Trust Resources.
How Does Zero Trust Compare to Traditional Models?
| Aspect | Traditional Security | Zero Trust Architecture |
|---|---|---|
| Trust Assumption | Assumes internal networks are secure | Assumes no one is inherently trustworthy |
| Access Control | Broad access once authenticated | Granular, least-privilege access |
| Monitoring | Limited to perimeter defenses | Continuous, real-time monitoring |
| Response to Breaches | Reactive | Proactive |
Real-World Examples of Zero Trust Success
Several organizations have successfully implemented Zero Trust to enhance their security posture:
- Google: After facing a major breach, Google adopted its proprietary BeyondCorp framework, which embodies Zero Trust principles.
- Microsoft: The tech giant uses Zero Trust to secure its global workforce and cloud infrastructure, emphasizing MFA and conditional access.
- U.S. Federal Government: In 2021, the White House issued an executive order mandating federal agencies to adopt Zero Trust by 2024.
For case studies, explore CSO Online’s Zero Trust Coverage.
A Paradigm Shift in Cybersecurity
Zero Trust Architecture represents a paradigm shift in how we think about cybersecurity. By abandoning the outdated notion of inherent trust and embracing continuous verification, organizations can build resilient defenses against modern threats. While implementation requires effort and commitment, the long-term benefits far outweigh the challenges.
As cybercriminals grow more sophisticated, adopting Zero Trust isn’t just a best practice—it’s a necessity. Start small, prioritize critical assets, and gradually expand your Zero Trust initiatives to safeguard your organization’s future. For ongoing updates, follow trusted sources like NIST Special Publications and Forrester’s Zero Trust Research.
In the fight against cybercrime, trust no one—but protect everyone.















Leave a comment